Best Dynamic Application Security Testing (DAST) Tool
Best dynamic application security testing software include insightvm, Veracode, HCL AppScan, netsparker, kondukto, and appknox are some that you can implement and use in 2024.



No Cost Personal Advisor
List of 20 Best Dynamic Application Security Testing Software
Emergents | 2024
Software by Acunetix
Invicti, originally known as Netsparker, is among the DAST tools that can detect flaws in legacy and advanced web apps, regardless of underlying technology or system. When the tool detects an exploitable flaw, its scanner employs Proof-Based ScanningTM technology to provide proof of the exploit, confirming that the outcome is not a false report. Learn more about Netsparker
Explore various Netsparker features, compare the pricing plans, and unlock the potential of seamless operations by selecting the right software for your business.
Features
View all Netsparker Features- IOC Verification
- Risk Management
- Vulnerability Assessment
- Database Security Audit
- Web Scanning
- Vulnerability Scanning
- Maintenance Scheduling
- Prioritization
Netsparker Caters to
- StartUps
- SMBs
- Agencies
- Enterprises
Contenders | 2024
Managed Website Security for Enterprises
The Indusface WAS software offers a completely controlled DAST solution. It is a negligible, non-intrusive cloud-based system that analyzes web applications daily, looking for system and application vulnerabilities and malware. With its automatic scans and manual pen testing performed by certified security specialists, Indusface WAS assures that no business logic defects or malware go undetected. Read Indusface WAS Reviews
Explore various Indusface WAS features, compare the pricing plans, and unlock the potential of seamless operations by selecting the right software for your business.
Features
View all Indusface WAS Features- Risk Assessment
- Web Scanning
- Web Traffic Reporting
- Vulnerability Scanning
- Risk Management
- Real Time Monitoring
Indusface WAS Caters to
- StartUps
- SMBs
- Agencies
- Enterprises
Emergents | 2024
Software by Acunetix
Acunetix (by Invicti) is a data protection and online vulnerability scanning system that uses automatic internet security techniques to scan and audit extensive, secured, HTML5, and JavaScript-heavy websites. Acunetix is among the dynamic application security testing tools that detect over 6,500 web vulnerabilities, including XSS, XXE, SSRF, SQL Injection, host header injection, and others. Learn more about Acunetix
Explore various Acunetix features, compare the pricing plans, and unlock the potential of seamless operations by selecting the right software for your business.
Features
View all Acunetix Features- Web Threat Management
- Risk Management
- Vulnerability Scanning
- Asset Discovery
- Compliance Management
- Audit Trail
- Database Security Audit
- Vulnerability Assessment
Acunetix Caters to
- StartUps
- SMBs
- Agencies
- Enterprises
Emergents | 2024
Software by Intruder
Intruder is a cloud-based vulnerability management software that assists with security tracking, risk evaluation, configuration mapping, and bug discovery. Security teams can use the dynamic analysis security testing solution to prioritize perimeter issues, detect unneeded exposure, and limit the attack surface. It monitors emerging threats by providing a unique risk interpretation system that simplifies vulnerability management Learn more about Intruder
Explore various Intruder features, compare the pricing plans, and unlock the potential of seamless operations by selecting the right software for your business.
Features
View all Intruder Features- Asset Tagging
- Vulnerability Assessment
- Risk Management
- Web Scanning
- Two-Factor Authentication
- Vulnerability Scanning
- Patch Management
- Prioritization
Pricing
Essential
$ 38
Per Month
Pro
$ 180
Per Month
Verified
$ 450
Per Month
Intruder Caters to
- StartUps
- SMBs
- Agencies
- Enterprises
Contenders | 2024
Software by Detectify
Detectify is a cybersecurity technology that assists programmers and security teams track assets and assess online application risk. With this dynamic application security testing (DAST) software, supervisors can track vulnerabilities such as DNS misconfigurations and SQL injections by adding domains or IP addresses, verifying asset ownership, scanning profiles, and generating reports. Read Detectify Reviews
Explore various Detectify features, compare the pricing plans, and unlock the potential of seamless operations by selecting the right software for your business.
Features
View all Detectify Features- Web Scanning
- Vulnerability Assessment
- Asset Discovery
Detectify Caters to
- StartUps
- SMBs
- Agencies
- Enterprises
Emergents | 2024
Software by StackHawk Inc.
StackHawk is among the DAST tools that simplify the discovery, triage, and resolution of application security flaws for developers. The tool can uncover vulnerabilities in a running environment instead of a static one which means you can be aware of dangers to your application in real-time.StackHawk provides a wealth of CICD and notification connectors. Learn more about StackHawk
Explore various StackHawk features, compare the pricing plans, and unlock the potential of seamless operations by selecting the right software for your business.
StackHawk Caters to
- StartUps
- SMBs
- Agencies
- Enterprises
Emergents | 2024
Software by Pentest Tools, Inc
Pentest-Tools finds and discloses flaws in webpages and network infrastructures. The DAST solution provides a collection of built-in pen testing tools that enable consumers to perform pentest engagements that are simpler, faster, and much more effective. It is the top cloud-based offensive security testing toolkit, specializing in web applications and network penetration testing. Learn more about Pentest Tools
Explore various Pentest Tools features, compare the pricing plans, and unlock the potential of seamless operations by selecting the right software for your business.
Pentest Tools Caters to
- StartUps
- SMBs
- Agencies
- Enterprises
Emergents | 2024
Software by Checkmarx Ltd
Checkmarx Static Application Security Testing (CxSAST) is a static analysis tool that helps firms uncover security bugs in source code. It is among the dynamic application security testing tools that enable teams of developers to automate workflows, set policies to simplify application system security and reduce operational risks. CxSAST assists users in performing safety tests and software composition assessments. Learn more about CxSAST
Explore various CxSAST features, compare the pricing plans, and unlock the potential of seamless operations by selecting the right software for your business.
Features
View all CxSAST Features- Diagnostic Tools
- Prioritization
- PCI Assessment
CxSAST Caters to
- StartUps
- SMBs
- Agencies
- Enterprises
Emergents | 2024
Software by Beagle Security, Inc
Beagle Security detects flaws in your web apps, APIs, and GraphQL and rectifies problems with actionable information before hackers do any damage. You can incorporate automated vulnerability scanning into your CI/CD workflow with the dynamic analysis security testing tool to uncover security concerns early in the development lifecycle and deploy safer online applications. Learn more about Beagle Security
Explore various Beagle Security features, compare the pricing plans, and unlock the potential of seamless operations by selecting the right software for your business.
Beagle Security Caters to
- StartUps
- SMBs
- Agencies
- Enterprises
Contenders | 2024
One-click testing with accurate results
HCL AppScan is a robust on-premises and cloud-based business application security testing tool package (SAST, DAST, IAST, SCA, API). It identifies application vulnerabilities and enables rapid remediation throughout the software development lifecycle. It is a dynamic application security testing (DAST) software that offers a perfect security scanner and numerous testing phases, ensuring accurate scan results and high testing quality. Read HCL AppScan Reviews
Explore various HCL AppScan features, compare the pricing plans, and unlock the potential of seamless operations by selecting the right software for your business.
HCL AppScan Caters to
- StartUps
- SMBs
- Agencies
- Enterprises
Contenders | 2024
Software by GitLab Inc
The GitLab DevSecOps platform fosters software innovation by enabling development, safety, and operations to create better software faster. Instead of maintaining multiple tools and scripts, teams can use GitLab to build, distribute, and manage code rapidly and constantly. GitLab is among the DAST tools that assist your teams across the DevSecOps lifecycle, from software development to security and deployment Read GitLab Reviews
Explore various GitLab features, compare the pricing plans, and unlock the potential of seamless operations by selecting the right software for your business.
Features
View all GitLab Features- Reporting/Analytics
- Deployment Management
- Debugging
- Collaboration Tools
- Data Modeling
- Mobile Development
- Software Development
- Access Controls/Permissions
Pricing
Free
$ 0
User/Month
Bronze
$ 4
User/Month
Silver
$ 19
User/Month
GitLab Caters to
- StartUps
- SMBs
- Agencies
- Enterprises
Contenders | 2024
Accelerate dynamic testing of applications and solutions
Veracode is a DAST solution that assists software innovators in delivering secure code on schedule. Veracode is a unique combination of SaaS technology and on-demand expertise that enables DevSecOps through pipeline integration, empowers developers to fix security defects, and scales your program through best practices to achieve your desired outcomes. Read Veracode Reviews
Explore various Veracode features, compare the pricing plans, and unlock the potential of seamless operations by selecting the right software for your business.
Veracode Caters to
- StartUps
- SMBs
- Agencies
- Enterprises
Contenders | 2024
Worlds most powerful mobile security tool
Appknox is a mobile application security service that employs an automated security testing suite to assist organizations in finding and fixing security problems. It is among the dynamic application security testing tools that have successfully reduced delivery deadlines, human expenses, and security threats. It is simple to use and has many API compatibilities. Read Appknox Reviews
Explore various Appknox features, compare the pricing plans, and unlock the potential of seamless operations by selecting the right software for your business.
Appknox Caters to
- StartUps
- SMBs
- Agencies
- Enterprises
Emergents | 2024
Embedding security as a service
Fortify on Demand (FoD) provides full app security. It provides a simple approach, to begin with, the ability to scale. Fortify on Demand provides in-depth phone app security assessment, open-source research, supplier app security management, and static and dynamic analysis security testing. False positives are deleted for each test, and application security specialists can personally evaluate test results. Learn more about Micro Focus Fortify
Explore various Micro Focus Fortify features, compare the pricing plans, and unlock the potential of seamless operations by selecting the right software for your business.
Micro Focus Fortify Caters to
- StartUps
- SMBs
- Agencies
- Enterprises
Emergents | 2024
Software by Rainforest
Rainforest is a QA solution that streamlines, automates the testing, and simplifies the execution of complex test suites with an API request. The dynamic application security testing (DAST) software enables teams to incorporate quality assurance methods directly into their development workflow and offloads test execution to an AI-powered execution engine for fast and scalable results. Learn more about Rainforest
Explore various Rainforest features, compare the pricing plans, and unlock the potential of seamless operations by selecting the right software for your business.
Rainforest Caters to
- StartUps
- SMBs
- Agencies
- Enterprises
Contenders | 2024
Software by PortSwigger
Burp Suite is used in most industries and big and small businesses. The software is a sophisticated group of tools for detecting and exposing vulnerabilities in web applications. It is among the DAST tools that offer a complete package ranging from a simple intercepting proxy to an advanced vulnerability scanner. Read Burp Suite Reviews
Explore various Burp Suite features, compare the pricing plans, and unlock the potential of seamless operations by selecting the right software for your business.
Features
View all Burp Suite Features- Incident Management
- Application Security
- Risk Management
- Prioritization
- Behavioral Analytics
- Transaction Monitoring
- Whitelisting / Blacklisting
- IOC Verification
Pricing
Pay as you scan
$ 1999
Per Year
Classic
$ 19121
Per Year
Unlimited
$ 49999
Per Year
Burp Suite Caters to
- StartUps
- SMBs
- Agencies
- Enterprises
Emergents | 2024
Software by Rapid7
AppSpider is an application safety and testing product that allows you to collect all the information required to test all the applications so that you are not left with gaps in application security. It is a DAST solution that crawls to the deepest corners of the most intricate apps to test for risk and provide users with the information needed to remediate fast. Learn more about AppSpider
Explore various AppSpider features, compare the pricing plans, and unlock the potential of seamless operations by selecting the right software for your business.
AppSpider Caters to
- StartUps
- SMBs
- Agencies
- Enterprises
Emergents | 2024
Modern Testing and breach elimination
Synopsys is one of the industry's greatest dynamic application security testing tools. With its Application Security Testing subscription, your organization can test and re-test any online or mobile app or external network at any depth and number of times. It gives unparalleled transparency, adaptability, and reliability at a consistent cost. Learn more about Synopsys
Explore various Synopsys features, compare the pricing plans, and unlock the potential of seamless operations by selecting the right software for your business.
Synopsys Caters to
- StartUps
- SMBs
- Agencies
- Enterprises
Emergents | 2024
Software by Qualys
Qualys Cloud Platform is a dynamic analysis security testing tool intended to assist enterprises in automating web application security, monitoring, and gaining visibility into the utilization of IT assets. It allows IT workers to detect hazards connected to illegal network access, perform audits and IP checks, and verify compliance with industry regulations. Learn more about Qualys Cloud Platform
Explore various Qualys Cloud Platform features, compare the pricing plans, and unlock the potential of seamless operations by selecting the right software for your business.
- Vulnerability Scanning
- Vulnerability Protection
- Audit Trail
- Compliance Management
- Security Event Log
- Database Security Audit
- Financial Data Protection
Qualys Cloud Platform Caters to
- StartUps
- SMBs
- Agencies
- Enterprises
Emergents | 2024
Software by TrustWave
Trustwave is the world's leading cloud-based regulation and information security provider. It is also one of the leading dynamic application security testing (DAST) software. The tool detects and responds to threats quickly. Trustwave professionals discover, evaluate, and eradicate cyber threats, reducing risk to the user's company and maximizing the user's return on investment by leveraging modern security technologies. Learn more about Trustwave
Explore various Trustwave features, compare the pricing plans, and unlock the potential of seamless operations by selecting the right software for your business.
Features
View all Trustwave Features- Anti Virus
- Web Threat Management
- Whitelisting / Blacklisting
- Activity Log
- Application Security
- Device management
Trustwave Caters to
- StartUps
- SMBs
- Agencies
- Enterprises
Dynamic application security testing (DAST) tools are vital when it comes to the security of an application. As technology continues to evolve, so do security threats. In 2024, staying ahead of these threats is more important than ever. Whether you're a developer, a security analyst, or an IT professional, understanding which DAST tools can provide the best protection for your applications can save you valuable time and resources.
Choosing the best DAST tool for your organization can be difficult with more than 130+ options on the market. Buyers should take into account a number of variables, such as coverage, accuracy, usability, integration, and pricing, in order to make an informed choice. This article will discuss the top DAST tools for 2024, their features, and a buyer's guide to assist you in choosing an appropriate solution.
What Are Dynamic Application Security Testing (DAST) Tools?
Dynamic application security testing (DAST) is a type of security testing that evaluates the security of an application by examining it from the outside in. It entails testing an application in real-time while assuming a possible attacker will take advantage of security flaws in the system. By simulating actual attack scenarios, DAST technologies give enterprises a non-intrusive way to evaluate the security of their applications.
These instruments can be used to assess an application's susceptibility to various attacks, including SQL injection, cross-site scripting (XSS), and other web-based exploits. DAST tools function by examining an application's inputs and outputs, locating weaknesses in the network architecture, and producing information on how to address these weaknesses.
Benefits Of Using Dynamic Application Security Testing (DAST) Tools
DAST solutions provide numerous advantages for organizations seeking to enhance their application security. Here we will see the benefits of utilizing DAST tools and how they contribute to an efficient and robust security testing process.

-
Flexibility
Flexibility in DAST solutions allows organizations to conduct security testing across multiple environments. These tools can be seamlessly integrated into various stages of the application development lifecycle, including development, staging, and production. By offering this versatility, DAST solutions enable comprehensive testing that covers the entire spectrum of application deployment.
-
Adaptability
DAST solutions demonstrate adaptability by accommodating diverse applications, frameworks, and technologies. These tools possess the capability to handle a wide range of software components, making them suitable for various scenarios. The adaptability of DAST solutions ensures that organizations can rely on a single tool to assess the security of their entire application landscape, regardless of the technologies or platforms involved.
-
Comprehensive testing
Comprehensive testing is a significant advantage of DAST solutions. These tools provide an in-depth examination of the entire application by actively scanning its functionality and simulating real-world attack scenarios. By emulating external threats, DAST solutions uncover security weaknesses that may go unnoticed by other testing methods, such as static analysis. With comprehensive testing, organizations can ensure that their applications are thoroughly evaluated and fortified against potential threats.
-
Identification of vulnerabilities
DAST solutions excel in the real-time identification of vulnerabilities. By scanning applications during runtime, these tools actively search for security flaws. They can detect issues like input validation vulnerabilities, configuration errors, and authentication weaknesses, among others. This minimizes the likelihood of successful attacks and strengthens the overall security posture of their applications.
-
Continuous assessment
Dynamic application security testing tools support continuous assessment of applications, ensuring that security testing is an ongoing and iterative process. With automated scans and regular testing cycles, organizations can proactively detect and remediate vulnerabilities as they arise. This maintains a proactive defense against potential threats.
-
User behavior simulation
User behavior simulation is a valuable feature offered by DAST tools. These tools enable organizations to simulate various user interactions and inputs, evaluating how the application responds to different scenarios. By mimicking attack vectors and manipulating user inputs, Dynamic analysis security testing assess the resilience of the application and identify potential vulnerabilities.
-
Cost savings and risk reduction
Dynamic application security testing (DAST) software brings about cost savings and risk reduction for organizations. By identifying weaknesses in the development process at an early stage, these utilities aid in avoiding potential security violations that might lead to monetary losses and harm to reputation. By automating security testing, firms can attain greater effectiveness, enabling their personnel to concentrate on other essential responsibilities.
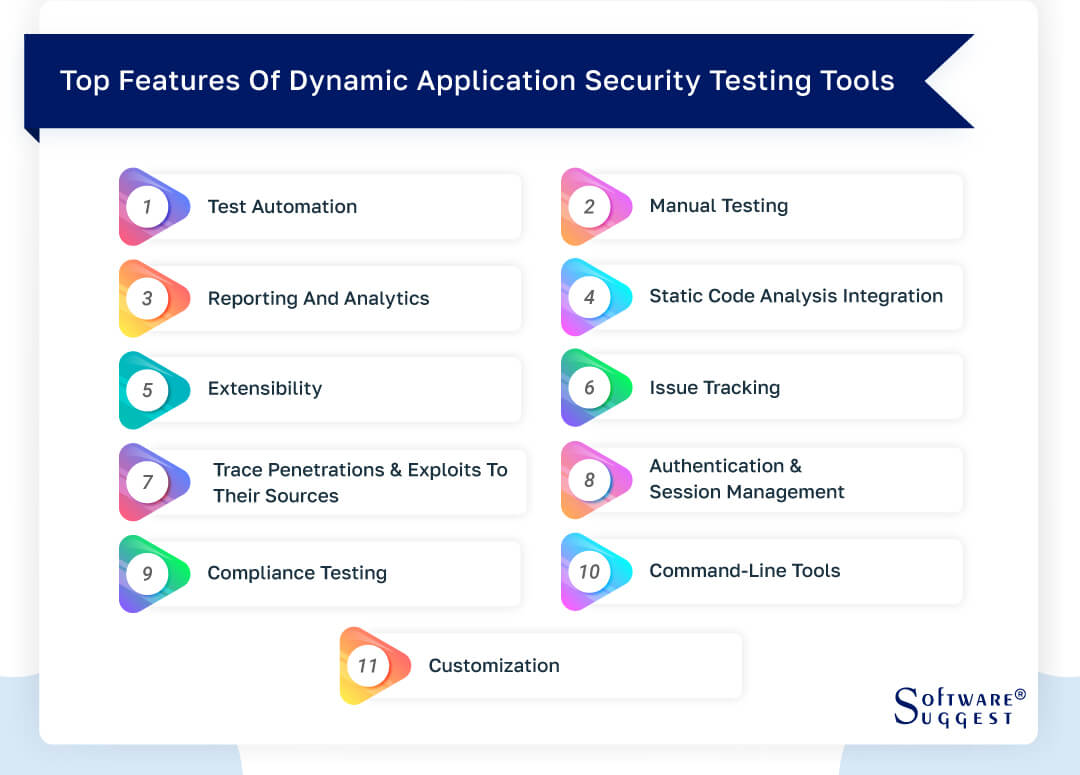
Common Features Of Dynamic Application Security Testing (DAST) Software
Dynamic Application Security Testing (DAST) software provides a range of features that enhance the effectiveness and efficiency of security testing processes. These common features provide establishments with the tools they need to identify vulnerabilities, automate testing, track issues, and enhance the overall security posture of their applications. Let's see them in detail.
-
Test automation
Test automation is a key feature of DAST software, enabling establishments to automate the scanning and testing of applications for security vulnerabilities. Without the need for manual assistance, DAST tools can automate repetitive processes like crawling around the application, sending queries, and analyzing answers. This capability provides complete and uniform testing across several applications while also saving time and effort.
-
Manual testing
While test automation is a critical feature, DAST software also allows for manual testing to supplement automated scans. Manual testing provides an opportunity for security testers to delve deeper into the application and perform targeted tests to uncover specific vulnerabilities. Manual testing enables intricate exploration of complex scenarios. The combination of automated scans and manual testing offers a comprehensive approach to security testing, ensuring that both known and unknown vulnerabilities are thoroughly assessed.
-
Reporting and analytics
Reporting and analytics capabilities are essential features of DAST software that enable organizations to communicate and track their security testing results effectively. DAST tools generate detailed reports that highlight identified vulnerabilities, their severity, and recommended remediation measures. These reports provide actionable insights for developers and security teams, facilitating the prioritization and resolution of security issues.
-
Static code analysis integration
DAST software often integrates with static code analysis tools, combining the strengths of both approaches to enhance security testing. Static code analysis allows for the early detection of security vulnerabilities by analyzing the source code of an application without its execution. This integration enables organizations to identify vulnerabilities that may not be apparent through purely dynamic testing and ensures a more comprehensive evaluation of the application's security.
-
Extensibility
The extensibility feature in DAST software allows organizations to customize and extend the capabilities of the tool according to their specific requirements. DAST tools often provide APIs and integration options that enable seamless integration with other security tools and continuous integration/continuous deployment (CI/CD) pipelines. This extensibility empowers organizations to tailor their security testing workflows and incorporate DAST within their existing development and deployment processes.
-
Issue tracking
DAST software empowers organizations to trace penetrations and exploits back to their sources. It facilitates a deeper understanding of the root causes behind security vulnerabilities. Through the analysis of attack paths and identification of exploited entry points, DAST tools assist organizations in effectively mitigating vulnerabilities. This capability enables the identification of potential weaknesses in the application's architecture, code, or configuration.
-
Trace penetrations and exploits to their sources
DAST software empowers organizations to trace penetrations and exploits back to their sources. It facilitates a deeper understanding of the root causes behind security vulnerabilities. Through the analysis of attack paths and identification of exploited entry points, DAST tools assist organizations in effectively mitigating vulnerabilities. This capability enables the identification of potential weaknesses in the application's architecture, code, or configuration.
-
Authentication and session management
The authentication of users and the management of their sessions are both essential to the security of applications. These facets are analyzed by the DAST software. It acts as a simulator for authentication processes, evaluating the efficacy of the mechanisms and discovering flaws such as insufficiently strong passwords and ineffective session management.
-
Compliance testing
Establishments operating in regulated sectors or adhering to specific security protocols must conduct compliance testing as a crucial aspect of their operations. The DAST system offers assistance for compliance testing, which entails evaluating apps against sector-specific norms, suggested practices, and regulatory requirements. These instruments can assess adherence to a range of requirements, including security controls, encryption techniques, data protection laws, and others.
-
Command-line tools
DAST software commonly incorporates command-line tools, adding flexibility and efficiency to security testing. Security professionals can execute scans, configure parameters, and analyze results using scripts or batch commands through command-line interfaces. This feature enables automation, seamless integration with other tools, and the incorporation of DAST software into existing workflows.
-
Customization
Customization is a valuable feature offered by DAST software, enabling organizations to tailor the tool to their specific needs and requirements. DAST tools often provide options for configuring scan settings, defining scanning policies, and adjusting vulnerability severity levels to align with the organization's risk tolerance. Customization capabilities allow organizations to fine-tune the tool's behavior, focus on specific areas of concern, and adapt to their unique application landscapes.
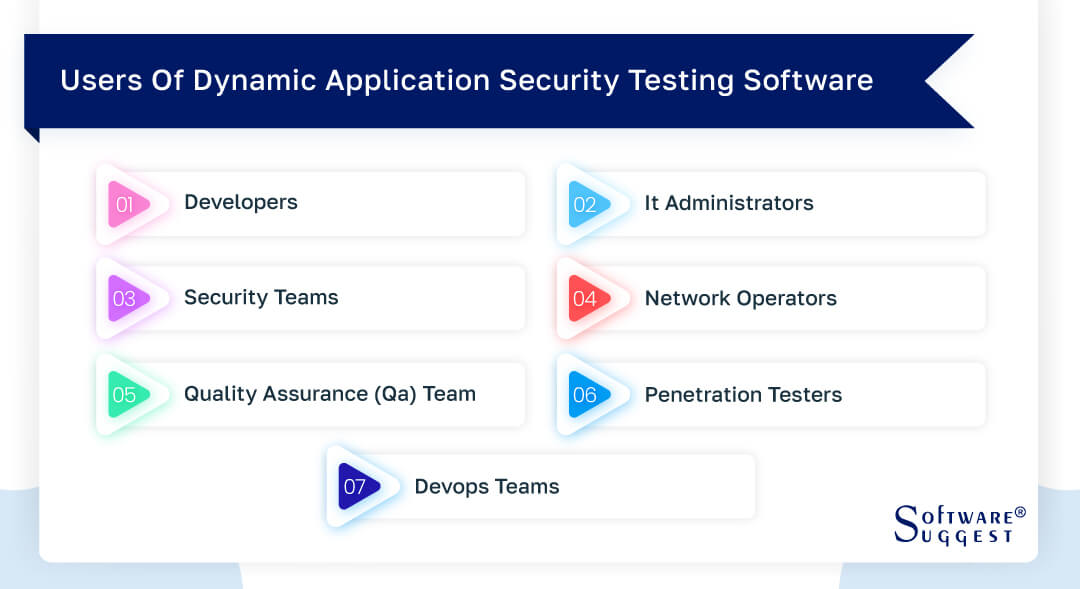
Who Uses Dynamic Application Security Testing (DAST) Software?
Dynamic application security testing (DAST) software plays a crucial role in ensuring the security of web applications. Let's explore how DAST software serves the needs of these user groups:
-
Developers
Developers are responsible for writing and maintaining the code of web applications. The development process can include thorough security testing thanks to DAST software. Developers can find holes and weak points in the application code by including DAST tools in their process. DAST software gives developers insightful feedback that aids in understanding potential security issues and directing them to create more safe code.
-
IT administrators
IT administrators play a critical role in managing and maintaining the infrastructure that supports web applications. IT managers can evaluate the security status of the apps they are in charge of using DAST software. It enables them to take proactive steps to fortify the security infrastructure, such as putting in place extra security measures or deploying the required patches.
-
Security teams
In the realm of safeguarding an organization's valuable assets and upholding security standards, the onus lies on security teams. Embracing the utilization of Dynamic Application Security Testing (DAST) tools emerges as a favorable approach for these teams seeking assistance. Such tools prove instrumental in unearthing vulnerabilities within web applications. This empowers them to establish priorities and address vulnerabilities based on their level of peril, thereby mitigating the overall risk posed to the organization's most critical assets.
-
Network operators
Tasked with the crucial duty of overseeing and upkeeping the intricate web of network infrastructure that underpins web applications, network operators shoulder immense responsibility. In order to assist them in this endeavor, the utilization of Dynamic Application Security Testing (DAST) software proves invaluable, enabling network operators to pinpoint security frailties lurking within network configurations and infrastructure elements. By initiating comprehensive DAST scans, network operators gain the ability to identify vulnerabilities present in critical network devices such as firewalls, routers, and load balancers.
-
Quality assurance (QA) team
It is the responsibility of the QA team to ensure the quality and dependability of web applications prior to their deployment. The employment of DAST software by the QA team proves advantageous as it facilitates comprehensive security testing. This enables them to offer constructive feedback to developers and guarantee that the application adheres to security protocols before it is launched.
-
Penetration testers
Penetration testers, who are also called "ethical hackers," are in charge of figuring out how safe web apps are by trying to break into them. DAST software is a valuable asset for penetration testers as it provides them with a comprehensive view of potential vulnerabilities in the application. This helps organizations proactively fix vulnerabilities before they are exploited, minimizing the risk of data breaches or unauthorized access.
-
DevOps teams
DevOps teams are responsible for the integration and delivery of software within an organization. DAST software is a crucial component of the DevOps toolkit, allowing teams to incorporate security testing into their continuous integration and deployment processes. This helps them identify and address security issues early on in the development lifecycle.
Pros And Cons Of Dynamic Application Security Testing
Dynamic Application Security Testing (DAST) offers both advantages and limitations in enhancing application security. Understanding the pros and cons of DAST helps organizations make informed decisions when implementing security testing methodologies.
-
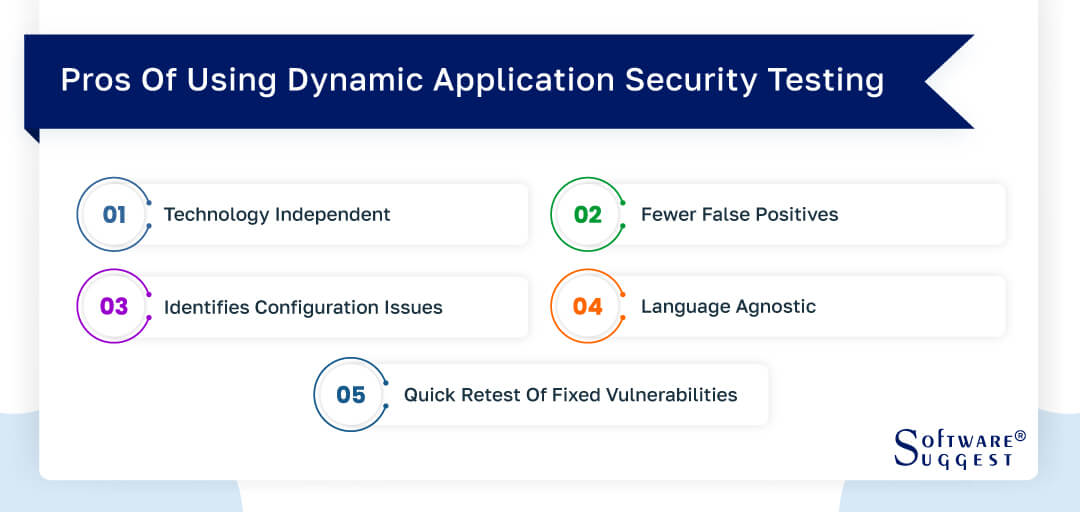
Pros Of DAST
DAST (Dynamic Application Security Testing) offers several advantages that contribute to its effectiveness in identifying vulnerabilities and improving the security of applications. These pros include:
-
Technology independent
DAST is technology independent, meaning it can be applied to a wide range of applications, regardless of the underlying technology stack or programming language. Whether it's a web application, mobile app, or API, DAST can effectively scan and test for security vulnerabilities, providing organizations with a versatile tool to assess the security of their diverse application landscapes.
-
Fewer false positives
DAST tools are designed to minimize false positives, reducing the number of erroneous vulnerability findings. By employing sophisticated scanning techniques and focusing on the actual runtime behavior of applications, DAST helps identify genuine security risks while minimizing the noise generated by false alarms. This enables security teams to concentrate their efforts on addressing real vulnerabilities and improving the overall accuracy and efficiency of their remediation efforts.
-
Identifies configuration issues
DAST excels at detecting configuration-related security issues. It can identify misconfigurations in servers, frameworks, databases, and other components of an application's infrastructure. By pinpointing these configuration weaknesses, DAST allows organizations to rectify potential security gaps that might otherwise be overlooked. This ensures that the application is not only secure at the code level but also properly configured to withstand potential attacks.
-
Language agnostic
DAST is language agnostic, meaning it can analyze applications written in various programming languages. Whether an application is developed in Java, Python, PHP, or any other language, DAST tools can effectively scan and test for security vulnerabilities. This flexibility allows organizations to assess the security of their applications regardless of the technology choices they have made, ensuring comprehensive coverage across their entire application portfolio.
-
A quick retest of fixed vulnerabilities
After addressing identified vulnerabilities, DAST enables organizations to quickly retest the fixes to ensure they have been properly implemented and the security gaps have been adequately closed. This feature allows for timely validation of remediation efforts, ensuring that vulnerabilities have been effectively patched and the application's security has been strengthened.
-
Cons Of DAST
While Dynamic Application Security Testing (DAST) offers several benefits, it also has certain limitations and drawbacks that organizations should be aware of. These cons include:
-
Not highly scalable
One of the challenges of DAST is that it may not be highly scalable, especially when dealing with large and complex applications. DAST tools often require significant computational resources and can be time-consuming when scanning extensive application landscapes. As a result, scalability can become an issue, making it challenging to perform comprehensive security testing on a large scale within limited timeframes.
-
No code visibility
Unlike other testing methodologies like Static Application Security Testing (SAST), DAST does not provide deep visibility into the application's source code. While it can identify vulnerabilities based on the application's behavior, it may not uncover code-level issues that require detailed code analysis. This lack of code visibility can limit the ability to pinpoint specific lines of code responsible for vulnerabilities, making it more challenging to address underlying coding flaws.
-
Results late in CI/CD pipeline
DAST is typically performed during the later stages of the software development lifecycle, such as the testing and deployment phases. As a result, security vulnerabilities may only be identified and addressed towards the end of the development process, potentially causing delays and rework. Waiting for DAST results late in the Continuous Integration/Continuous Deployment (CI/CD) pipeline can disrupt the development flow and may require additional iterations to remediate the identified vulnerabilities.
-
Manual testing may be required
While DAST tools automate a significant portion of the security testing process, there are instances where manual testing becomes necessary. Complex business logic scenarios, edge cases, or application-specific vulnerabilities may require human intervention and expertise to detect. This means that organizations may still need to allocate resources for manual testing alongside DAST to achieve comprehensive coverage and identify more nuanced security issues.
-
Slow scans
DAST scans can be time-consuming, especially when evaluating large and complex applications. The process involves interacting with the application in real-time, mimicking user behavior, and analyzing responses. This thorough approach, while beneficial for accuracy, can result in slower scan times compared to other automated security testing methods. The longer scan durations can impact productivity, especially when organizations aim to maintain agile development cycles and deliver applications promptly.
Steps For Implementation Of Dynamic Application Security Testing (Dast) Tool
Implementing a dynamic application security testing (DAST) tool involves a series of strategic steps to ensure effective security testing of applications. These steps aim to align the tool with organizational goals and integrate it seamlessly into the development process.
-
Discuss your user needs
The first step in implementing a DAST tool is to sit down with the users who will be involved in the security testing process. Recognize your customers' needs, goals, and expectations. Gather information on the specific security threats and concerns and talk about the size of the application landscape that needs to be evaluated. The installation of the DAST tool will be in line with the organization's security objectives. It will take into account the particular needs of the application ecosystem thanks to this collaborative approach.
-
Automate interactions
To effectively utilize a DAST tool, it is crucial to automate interactions with the application being tested. This involves creating scripts or leveraging automation frameworks that simulate user behavior, such as login, form submission, navigation, and data input. By automating interactions, organizations can ensure consistent and repeatable testing scenarios, enabling comprehensive security testing across various application states and user workflows.
-
Adding test scripts to CI/CD
Integrating the DAST tool into the Continuous Integration/Continuous Deployment (CI/CD) pipeline is a vital step for seamless security testing. By incorporating test scripts into the CI/CD process, security scans can be triggered automatically as part of the build and deployment stages.
-
Addition of regression tests to the testing suite
As the DAST tool identifies vulnerabilities and security issues, it is essential to add these tests to the organization's existing testing suite as regression tests. These tests should be executed regularly. It is to ensure that previously identified vulnerabilities remain remediated. Also, no new vulnerabilities are introduced during subsequent code changes or deployments.
Common Tips For Using Dynamic Application Security Testing (DAST) Tools
Implementing effective security testing with a Dynamic Application Security Testing (DAST) tool requires careful consideration and adherence to best practices. These tips help organizations maximize the benefits of DAST in securing their applications.

-
Use DAST early and often for the best results
In order to maximize the benefits of a DAST tool, it is crucial to incorporate it early in the software development lifecycle. By conducting security testing with DAST from the initial stages of application development, vulnerabilities can be identified and addressed promptly, reducing the overall risk exposure.
Additionally, regular and frequent use of the DAST tool throughout the development process allows for continuous security assessment, enabling proactive vulnerability management and ensuring that potential security issues are addressed before they become more significant and costly.
-
Enable effective collaboration with DevOps
Successful utilization of a DAST tool requires effective collaboration between security teams and DevOps. Establishing clear lines of communication and integrating security testing into the DevOps workflow ensures that security becomes an integral portion of the development process.
By involving both security and development teams, potential security vulnerabilities can be identified early on, and remediation efforts can be aligned with the development cycle. Collaboration also facilitates the sharing of knowledge, best practices, and the incorporation of security requirements into the application development and deployment processes.
-
Follow a comprehensive approach to web application
Although DAST technologies are useful for locating vulnerabilities in online applications, they work best when integrated into a thorough strategy for web application security. To create a comprehensive security assessment, DAST should be used with other testing approaches like Static Application Security Testing (SAST) and manual security assessments.
Each testing method brings its own unique benefits and insights, and by combining them, organizations can uncover a wider range of vulnerabilities and strengthen their overall security posture.
Considerations While Selecting Dynamic Application Security Testing (DAST) Tools
Selecting the right Dynamic Application Security Testing (DAST) tool requires careful consideration of various factors. Let's learn each of them in detail:

-
Understand your web application and environment
Before selecting a DAST tool, it is crucial to have a thorough understanding of your web application and its environment. Evaluate the complexity and intricacies of your application, including its technology stack, architecture, and any unique components such as web frameworks, APIs, mobile applications, or cloud environments.
-
Know your business needs
It is vital to precisely identify both your needs and your goals in order to choose the DAST solution that will best meet your requirements. Take into mind not only the acceptable level of competence for the security testing but also the breadth of the testing. Also, don't forget the security goals of your establishment. Establish the testing requirements while keeping in mind the specific compliance standards that have to be attained.
-
Ensure compatibility
Ensuring compatibility with your existing technology stack is a critical consideration when selecting a DAST tool. Verify that the tool supports the programming languages, frameworks, platforms, and databases used in your web application. Assess whether it integrates seamlessly with your development and testing environments, including your IDEs, build systems, and version control systems.
-
Assess coverage capabilities
When evaluating DAST tools, it is important to assess their coverage capabilities. Look for tools that offer comprehensive scanning and testing for common vulnerabilities, such as injection attacks, cross-site scripting (XSS), cross-site request forgery (CSRF), and others. Consider whether the tool provides coverage for both front-end and back-end components of your application, as well as APIs and mobile applications.
-
Evaluate licensing options
Consider the licensing options available for the DAST tool. Assess whether a commercial license or an open-source solution best fits your organization's needs and budget. Understand the limitations and perks associated with each licensing model. Evaluate factors such as ongoing maintenance and support services provided by the vendor or the open-source community.
-
SDLC integration
Integration with your Software Development Life Cycle (SDLC) is crucial for efficient and effective security testing. Look for DAST tools that seamlessly integrate with your existing development and testing processes. Consider features such as integration with Continuous Integration/Continuous Deployment (CI/CD) pipelines and support for automation.
-
Evaluate the scalability
Evaluate the scalability of the DAST tool to ensure it can meet your organization's future needs. Consider its performance when testing large-scale applications or when multiple applications need to be tested concurrently. Assess the tool's ability to handle the increased workload and its capacity to scale as your application portfolio expands.
-
Level of support and community
When selecting a DAST tool, it is important to evaluate the level of support and community engagement associated with it. Consider factors such as vendor support, access to documentation, training resources, and the availability of a user community or online forums for knowledge sharing.
Top 5 Dynamic Application Security Testing (DAST) Tools: Comparison
We curated a collection of the top 5 Dynamic application security testing (DAST) tools. These powerful solutions provide thorough vulnerability assessments for web applications. Explore our expert recommendations to discover the leading DAST tools that enable establishments to identify and address security risks effectively, ensuring robust application security.
|
Name
|
Free Trial
|
Demo
|
Starting Price
|
|---|---|---|---|
Acunetix |
14 Days |
Yes |
On request |
Astra Pentest |
7 Days |
Yes | $1,999/year |
Veracode |
30 Days |
Yes |
On request |
GitLab |
14 Days |
Yes |
$29/month |
Detectify |
14 Days |
Yes |
On request |
1. Acunetix
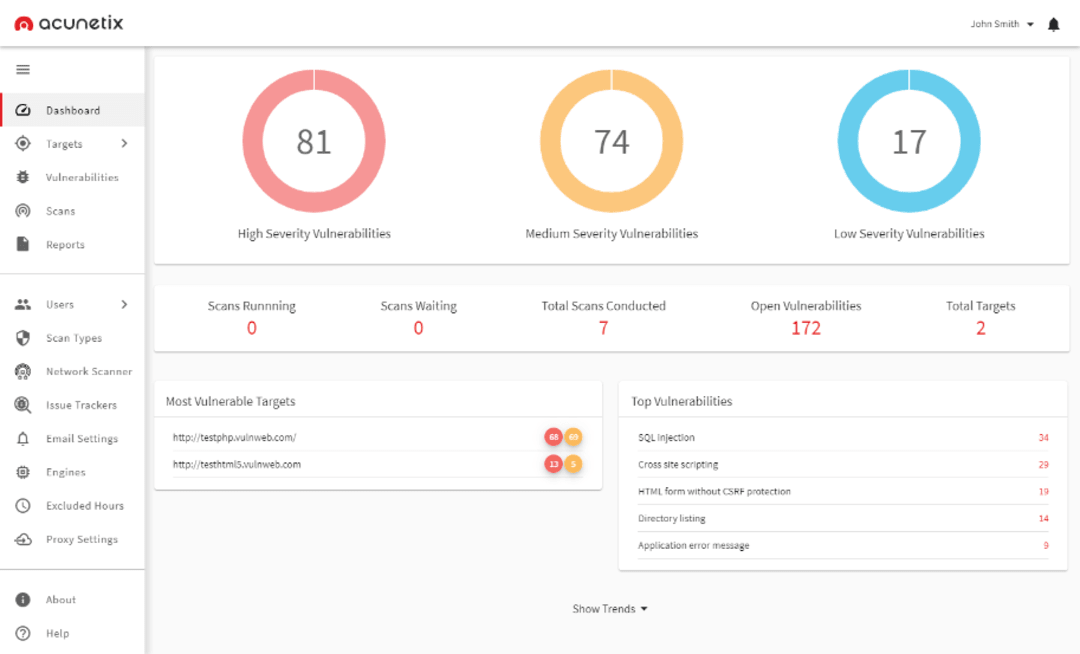
Acunetix, developed by Acunetix Ltd, is a web application security software designed to help safeguard web applications and websites against various security vulnerabilities. Its primary objective is to identify hazards like SQL injection, cross-site scripting (XSS), and other comparable problems. Security consultants, IT managers, website owners, and security experts all make heavy use of Acunetix.
This is done to properly identify and handle any potential security vulnerabilities. It provides a wide range of features like auditing, reporting, compliance checking, and more through both cloud-based and on-premise solutions. Additionally, Acunetix creates thorough reports identifying potential risks and offering suggestions for remedy.
Features
- Advanced web application security scanner
- Integration with DevOps and issue-tracking tools
- Cloud-based architecture
- Software composition analysis
- Comprehensive reporting
- Network scanning
Pros
- Acunetix detects 7,000+ web vulnerabilities with its advanced web app scanner
- It has an intuitive interface for easy navigation and comprehensive security assessments
- It provides a holistic view of vulnerabilities with combined DAST and IAST scan results
- Its SCA feature scrutinizes open-source components to mitigate risks from third-party libraries
- It integrates with CI/CD pipelines and issue-tracking tools for streamlined security processes
- Its flexible API allows for smooth integration with other systems and customization
- It has a 99% customer satisfaction rate and exceptional customer support
Cons
- Acunetix's features may be challenging for new users, making it a steep learning curve
- Acunetix requires significant computing resources, which may impact system performance
Pricing
- Custom Pricing.
2. Astra Pentest
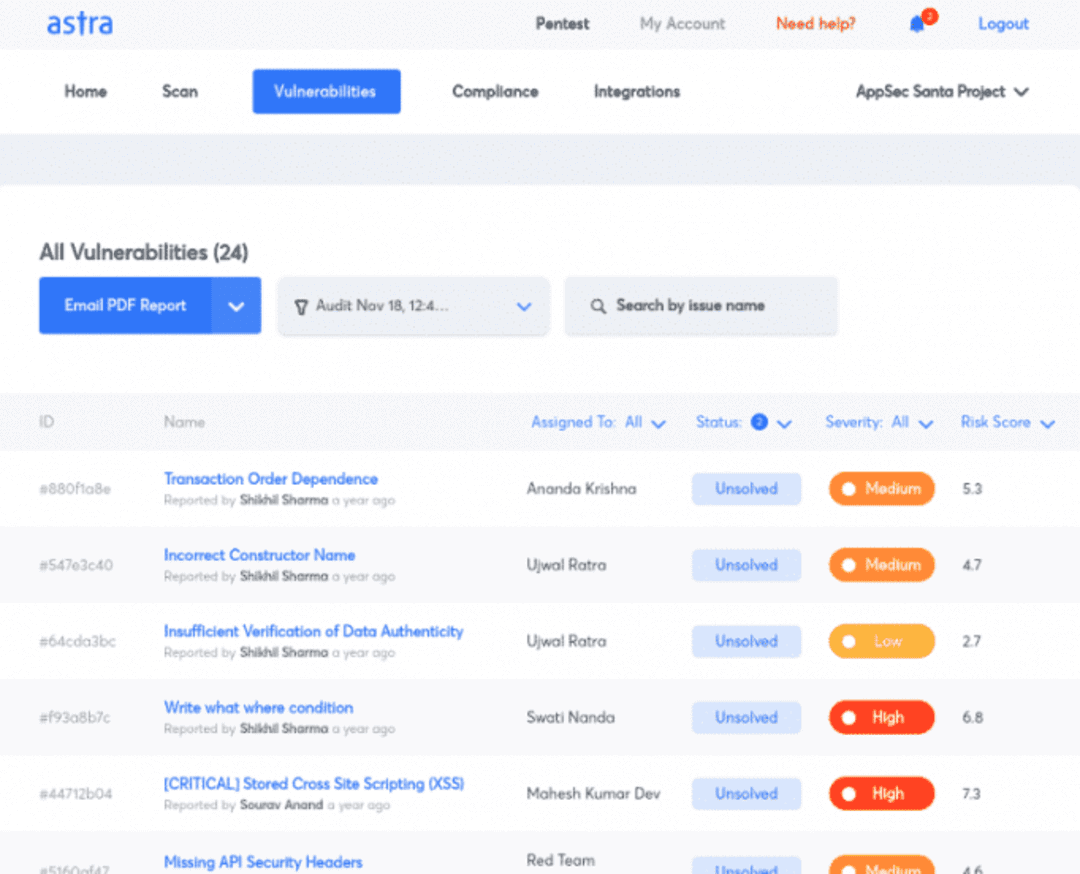
Astra Pentest is a powerful solution developed by the Astra company. This software is specifically designed to enhance the security of web applications. By conducting comprehensive penetration testing, Astra's software assists in identifying and addressing vulnerabilities within web applications.
Also, ensures robust protection against potential attacks. The primary goal of Astra's web application security software is to provide web application owners, developers, and security professionals with the necessary tools to identify and mitigate security risks effectively.
Features
- Vulnerability scanner
- Reporting & dashboard
- Manual pentest
- Interactive application security testing
- Certificate
- Integrations
Pros
- It automates security testing without manual intervention
- Clear reports outline vulnerabilities found and steps for remediation
- Immediate alerts for new vulnerabilities or security issues
- Tailor scans to focus on critical areas of your website
- Seamlessly integrates with DevOps and issue-tracking systems for streamlined security in the development
Cons
- Requires time and effort to understand and effectively use all features
- It has limitations with certain technologies, frameworks, or environments, affecting vulnerability detection
Pricing
- Scanner- $1,999 per year
- Pentest- $4,999 per year
- Enterprise- $6,999 per year
3. Veracode
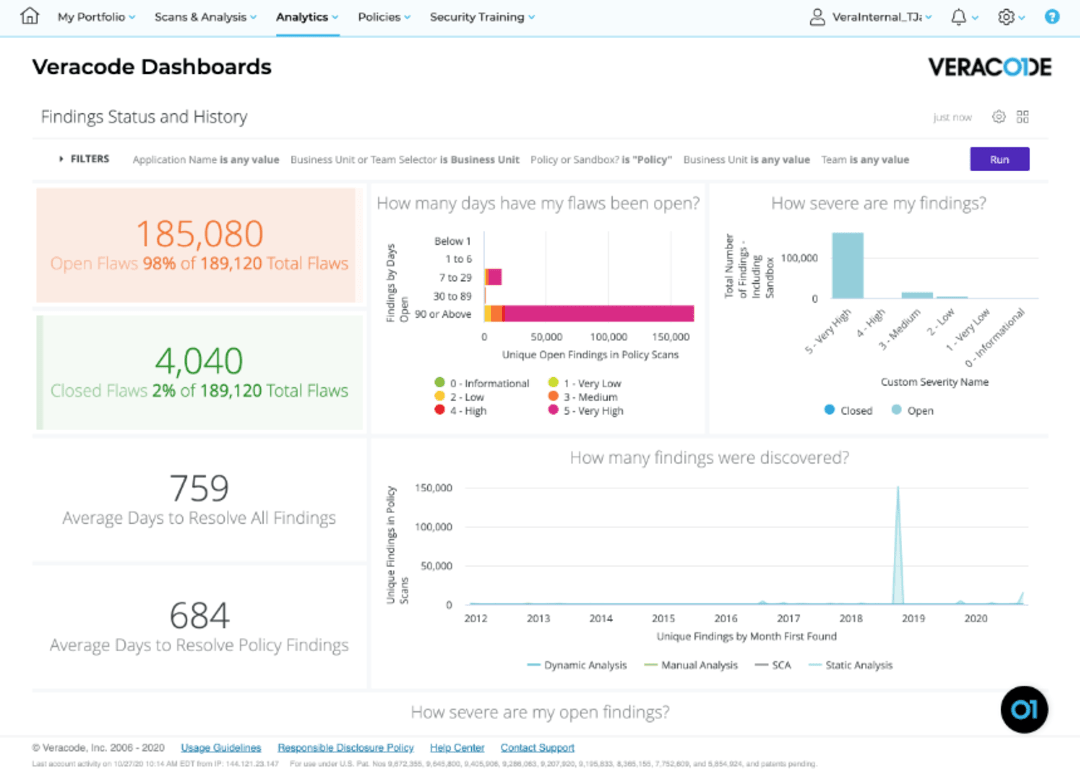
Veracode's Dynamic Analysis (DAST) software is a cutting-edge solution designed to secure your web applications. This state-of-the-art answer has the capability to identify weaknesses instantly, guaranteeing the ongoing safety of your applications against any potential cyber threats.
By prioritizing user experience, DAST enables enterprises to establish credibility with their clients and safeguard their brand reputation. By employing a data-oriented approach, their technique ensures continuous surveillance and practical feedback. Hence facilitating prompt adaptation to changing security patterns.
Features
- Powerful scan engine
- Combined crawl & audit
- Web app & API scanning
- Granular scan control
- Pre-production scanning
- Reporting & automated ticketing
Pros
- Veracode's DAST excels in comprehensive vulnerability detection for thorough security assessments
- It offers a scalable and flexible architecture, accommodating different application sizes and complexities
- Detailed reports provide a clear overview of identified vulnerabilities and recommended mitigation steps
- Seamless integration with the development workflow enables proactive vulnerability mitigation
- Excellent customer support and additional resources assist users in maximizing the benefits
Cons
- The learning curve associated with utilizing all features of Veracode's DAST solution
- Possibility of false positives, requiring additional time and effort for verification
Pricing
- Custom pricing.
4. GitLab
GitLab is a software development company that provides a complete DevOps platform for building, testing, and deploying software. It provides an extensive array of software tools and services encompassing source code management, continuous integration and deployment, monitoring, security, and more. It aims to foster collaboration and enhance productivity among teams.
Notably, this company operates in a fully remote manner, with employees situated globally, setting it apart from others. This unique characteristic enables them to create a flexible and inclusive work environment that attracts professionals from diverse backgrounds. GitLab, the company in question, is dedicated to pushing the limits of software development and deployment, and numerous businesses worldwide depend on its inventive platform.
Features
- Dynamic application security testing
- Security dashboards
- Vulnerability management
- Dependency scanning
- Container scanning
- Static application security testing
- Multi-level epics
Pros
- Comprehensive DevOps platform with source code management, CI/CD, monitoring, and security
- Remote collaboration appeals to professionals worldwide
- Continuous innovation and evolution of the platform
- Native integrations with CI/CD and issue tracking tools for seamless workflow integration
- Reliable customer support for assistance and resources
Cons
- The learning curve for GitLab's comprehensive platform
- Complexity in customizing the platform
Pricing
- Free
- Premium- $29 per user per month
- Ultimate- $99 per user per month
5. Detectify
Detectify is a cybersecurity company that provides automated web application security testing as a service. Their product enables businesses to monitor their security posture and discover important vulnerabilities. Utilizing sophisticated custom exploits as well as popular content management system exploits, Detectify continuously scans online apps for vulnerabilities.
The establishment also provides a number of extra services, such as web API security testing and vulnerability disclosure programs. Detectify, a web application security solution company with headquarters in Stockholm, Sweden, was founded in 2013 and is regarded as a market leader by some of the world's most security-conscious companies.
Features
- Dashboard & reporting
- Alerting
- Vulnerability assessment
- Security auditing
- Performance
- Issue tracking
- Detection rate
Pros
- Continuous 24/7 coverage provides daily insights on every exposed asset in your tech stack
- Unique crawling and fuzzing engine surpasses traditional DAST scanners
- Ability to monitor large enterprise products and protect sensitive data from hackers
- Accurate results save time, with 99.7% accuracy in vulnerability assessments through payload-based testing
- Exclusive features include SSO, API access, bypass/automatic domain verification, custom modules, and customizable attack surface policies
- Proactively identify risks by enriching assets with critical information like open ports, DNS record types, and technologies
Cons
- The learning curve is steep to use all of this solution's features
- Potential for false positives, which would require more time and work to confirm
Pricing
- Custom pricing.
Software That Integrates With the Dynamic Application Security Testing (DAST) Tool
Various software integrates with DAST tools, enhancing security testing by detecting vulnerabilities in real-time during application runtime. Also, it helps organizations proactively address potential cyber threats and safeguard their applications. Let's look at the following software in detail:
-
Static code analysis software
Static code analysis software is a valuable tool for developers and security professionals alike. It can find weaknesses and flaws in the codebase by looking at the source code without running it. It helps find problems like coding mistakes, unsafe ways of writing code, and possible security holes.
-
Static application security testing (SAST) software
Static application security testing (SAST) software plays a critical role in ensuring the security of software applications. It analyzes the source code and identifies security weaknesses, vulnerabilities, and coding errors. Unlike Dynamic Application Security Testing (DAST) tools, which test applications during runtime, SAST tools focus on examining the code itself.
-
Vulnerability scanners
Vulnerability scanners are essential tools for organizations aiming to maintain a secure software environment. These scanners actively search for known vulnerabilities in applications, networks, and systems. By identifying weaknesses in software components, configurations, or network infrastructure, vulnerability scanners help prevent potential attacks and data breaches.
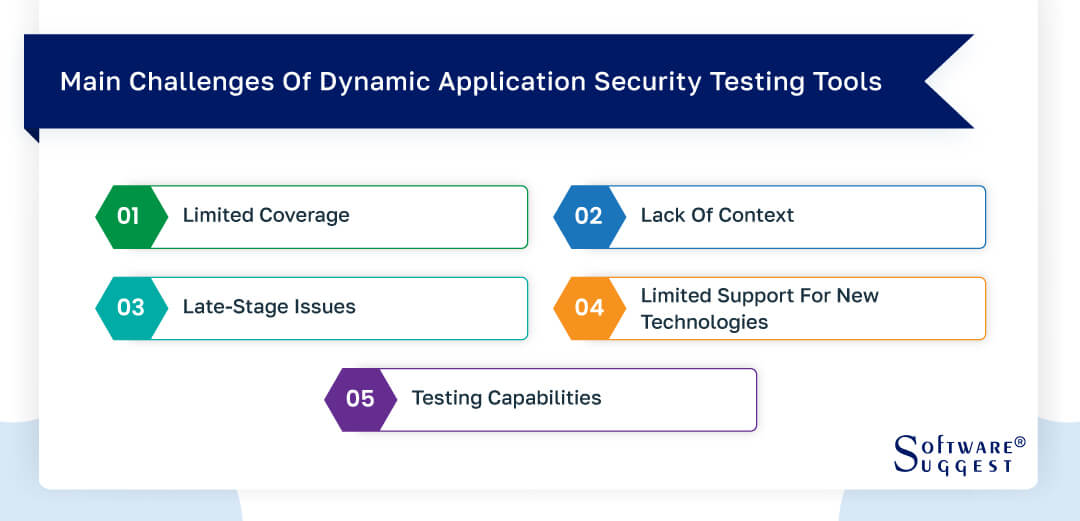
Challenges Of Dynamic Application Security Testing (DAST) Tools
Dynamic application security testing (DAST) tools are essential for identifying vulnerabilities in web applications, but they come with their own set of challenges. Let's see them in detail:
-
Limited coverage
When it comes to the realm of dynamic application security testing (DAST) tools, there exist a number of challenges that security teams and network operators must navigate. One such challenge is the limited coverage provided by these tools. DAST tools serve as valuable assets in identifying security weaknesses within web applications.
However, their effectiveness relies on their ability to comprehensively scan and assess the entire application landscape. However, due to the ever-evolving nature of web applications and their complex architectures, DAST tools may struggle to provide extensive coverage, leaving certain areas untested and potentially vulnerable to attacks.
-
Lack of context
Another challenge that arises with DAST tools is the lack of context they often encounter. In their quest to identify security holes, DAST tools rely heavily on automated scanning techniques. This approach enables a thorough analysis of application vulnerabilities.
However, it may fall short of providing a deeper understanding of the application's specific context. Without context, the generated findings from DAST tools can be overwhelming for security teams, leading to difficulties in prioritizing and addressing the identified issues effectively.
-
Late-stage issues
One of the significant challenges of relying solely on DAST tools for security testing is the tendency to uncover vulnerabilities in the late stages of the development cycle. DAST tools typically operate by scanning the running application, meaning they are deployed after the application is built and deployed in a production environment.
This delayed approach to security testing can result in the identification of critical issues when they are more expensive and time-consuming to fix. Ideally, security testing should be integrated early in the development process to proactively address vulnerabilities and minimize the risk of late-stage discoveries.
-
Limited support for new technologies
As technology continues to advance at a rapid pace, the challenge of keeping up with new developments poses a hurdle for DAST tools. Emerging technologies and frameworks often introduce unique security considerations and require specialized testing approaches. However, DAST tools may lag behind in terms of supporting new technologies.
This can leave security teams grappling with limited testing capabilities. To ensure comprehensive security coverage, it becomes crucial for DAST tool developers to stay abreast of the latest technological trends and continuously enhance their tools to cater to evolving application landscapes.
-
Testing capabilities
While DAST tools excel in identifying vulnerabilities within web applications, they may exhibit limitations when it comes to certain testing scenarios. For instance, DAST tools primarily focus on the application's external interfaces and may not delve deep into the underlying code or business logic.
This limitation restricts their ability to detect certain types of vulnerabilities that reside within the application's internal structure. To address this challenge, organizations often employ a combination of testing techniques, such as static analysis and penetration testing, alongside DAST tools to ensure comprehensive coverage and mitigate the risk of undiscovered vulnerabilities.
How Much Does Dynamic Application Security Testing (Dast) Software Cost?
DAST software costs between $50 and more than $400 a month, depending on the user. Other pricing models take into account how big the company is and how many apps are being tested. Some DAST tools let you try them out for free, while others let you set your own price based on your needs. Researching and comparing DAST tools can help an organization find the right one for its budget and security testing needs.
Conclusion
In the quest for the best Dynamic Application Security Testing (DAST) tool, thorough research and user feedback have identified several outstanding options. Each of the top contenders offers unique strengths to meet diverse security needs.
Acunetix impresses with its comprehensive scanning capabilities, while Astra Pentest stands out for its user-friendly interface. Veracode shines with accurate and actionable results, GitLab excels in seamless integration, and Detectify offers a vast library of security checks.
Ultimately, the choice depends on specific requirements and priorities. Organizations should consider factors like scanning efficiency, reporting capabilities, ease of use, and support to select the ideal DAST tool that strengthens their application security.






















