Tenable Nessus
What is Tenable Nessus?
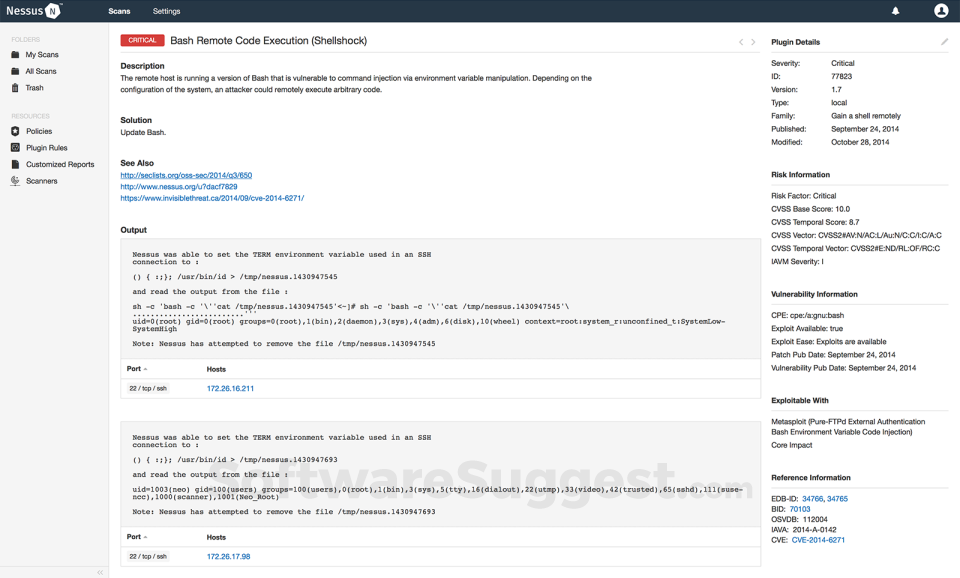
Nessus is a fully featured Vulnerability Management Software designed to serve Enterprises, Startups. Nessus provides end-to-end solutions designed for Windows. This online Vulnerability Management system offers Network Scanning, Vulnerability Assessment, Asset Discovery, Policy Management, Web Scanning at one place.
Tenable Nessus Starting Price

Our Awards and Recognition
Talk with a software expert for free. Get a list of software that's great for you in less than 10 minutes.
Key Features of Tenable Nessus
Here are the powerful features that make Tenable Nessus stand out from the competition. Packed with innovative tools and advanced functionalities, this software offers a range of benefits.
- Asset Discovery
- Asset Tagging
- Asset Discovery
- Asset Tagging
- Compliance Reporting
- Compression
- Continuous Backup
- Database Security Audit
- Diagnostic Tools
- IOC Verification
- Local Server Options
- Maintenance Scheduling
- Multiple System Support
- Network Scanning
- Patch Management
- PCI Assessment
- Access control
- Application Security
- Application Security Orchestration and Correlation (ASOC)
- Application Server
- Applied Behavior Analysis (ABA)
- Authentication and Authorization
- Code Review
- Compliance monitoring
- Content Security Policy (CSP)
- Cross-Site Request Forgery (CSRF) Prevention
- Cross-Site Scripting (XSS) Prevention
- Data Encryption
- DevSecOps
- Dynamic Application Security Testing (DAST)
- Electronic medical records (EMR)
- Error handling and logging
- API Security Assessment
- Application Scanning
- Asset Discovery
- Asset Inventory Management
- Attack Surface Analysis
- Cloud Security Assessment
- Compliance Reporting
- Configuration Assessment
- Continuous Monitoring
- Database Scanning
- Exploit Detection
- Host Intrusion Detection System (HIDS)
- Log Analysis
- Malware Detection
- Misconfiguration Detection
- Network Intrusion Detection System (NIDS)
- Brute-Force Attack Simulation
- Command Execution Testing
- Compliance Testing
- Continuous Monitoring and Testing
- Cross-Site Scripting (XSS) Testing
- Denial of Service (DoS) Testing
- Directory Traversal Testing
- DNS Spoofing
- Exploit Generation
- File Inclusion Testing
- Firewall and Intrusion Detection System (IDS) Testing
- Malware Analysis
- Man-in-the-Middle (MitM) Attacks
- Multi-Platform Support
- Network Mapping
- Password Cracking
- API and Web Service Security Testing
- Authentication and Session Management Testing
- Authorization and Access Control Testing
- Automated Vulnerability Detection
- Business Logic Testing
- Compliance Testing (e.g.
- PCI DSS
- HIPAA)
- Continuous Integration (CI) and Continuous Deployment (CD) Integration
- Cookie Security Testing
- Cross-Site Request Forgery (CSRF) Testing
- Cross-Site Scripting (XSS) Testing
- Directory Traversal Testing
- Dynamic Application Security Testing (DAST)
- File Upload Security Testing
- Fingerprinting of Web Technologies
Tenable Nessus Specifications
Get a closer look at the technical specifications and system requirements for Tenable Nessus. Find out if it's compatible with your operating system and other software.
Tenable Nessus Comparisons
Compare Tenable Nessus with other similar options available in Vulnerability Management Tools. Explore the key differences to see why it's the top choice for businesses and individuals.

Tenable Nessus Videos
Overall Tenable Nessus Reviews
Thinking about using Tenable Nessus? Check out verified user reviews & ratings based on Tenable Nessus's features, user-friendliness, customer support, and other factors that contribute to its overall appeal.
Tenable Nessus Pros and Cons
"The false-positive rate is too low. Easy to use and user-friendly makes me impressed. Technical staffs both local partners and vendor are willing to help. The other thing the most important is to create new signatures for the latest vulnerabilities quickly and The Nessus does."
"The myriad features, the ease of use and the relatively low resource consumption"
"I think they need to improve their reporting features. I can not get a pdf report on the Professional license."
"In some cases, Nessus is known to give false positives. However, this is more annoying then concerning as we have learned to identify them and verify their authenticity"
2 Tenable Nessus Reviews
Hear directly from customers who have used Tenable Nessus. Read their experiences, feedback, and ratings to gain valuable insights into how this software has benefited their businesses.
barisg.
Security Consultant
Used the software for : 2+ years (Weekly)
Company Size :51-200 employee
Nessus is the best vulnerability management tool
I think and relate to my experience Nessus is the best security vulnerability tool. I can easily find the vulnerabilities in my network. The false-positive rate is low.
Tenable Nessus Mobile App Experience
Tenable Nessus After Sales Service Rating
What do you like best about Tenable Nessus?
The false-positive rate is too low. Easy to use and user-friendly makes me impressed. Technical staffs both local partners and vendor are willing to help. The other thing the most important is to create new signatures for the latest vulnerabilities quickly and The Nessus does.
What do you dislike about Tenable Nessus?
I think they need to improve their reporting features. I can not get a pdf report on the Professional license.
What features is Tenable Nessus currently missing?
PDF Reporting
What other products like Tenable Nessus have you used or evaluated?
Rapid 7,OpenVas
How Tenable Nessus is better/different from its competitors?
Quick and low false-positive rate and technical support
AsifB.
Used the software for : 2+ years
Company Size :51-200 employee
Nessus Vulnerability Scanner Review
Nessus has significantly simplified vulnerability assessment and penetration testing engagements. Its ease of use and numerous features make it a must-have tool for any network security engagement. Additionally, there are modules for various additional tasks, such as compliance scanning as per CIS, NIST, and even PCI DSS. Also, one can even use it to carry out a preliminary application security assessment. The availability of conducting credentialed scanning makes it simple to perform scanning of missing patches remotely for a large number of devices. All in all, an excellent and must have a tool
Tenable Nessus Mobile App Experience
Tenable Nessus After Sales Service Rating
What do you like best about Tenable Nessus?
The myriad features, the ease of use and the relatively low resource consumption
What do you dislike about Tenable Nessus?
In some cases, Nessus is known to give false positives. However, this is more annoying then concerning as we have learned to identify them and verify their authenticity
Do you think Tenable Nessus delivers value for the money spent?
Yes
Are you satisfied with Tenable Nessus features?
Yes
Did implimentation of Tenable Nessus was easy?
Yes
What features is Tenable Nessus currently missing?
No
What other products like Tenable Nessus have you used or evaluated?
Open VAS
How Tenable Nessus is better/different from its competitors?
Nessus has more features, is user friendly and cheaper
Alternatives of Tenable Nessus
Explore alternative software options that can fulfill similar requirements as Tenable Nessus. Evaluate their features, pricing, and user feedback to find the perfect fit for your needs.
Tenable Nessus FAQs
What are the top 5 features for Tenable Nessus?
The top 5 features for Tenable Nessus are:
- Policy Management
- Prioritization
- Asset Discovery
- Network Scanning
- Vulnerability Assessment
What type of customer support is available from Tenable Nessus?
The available support which Tenable Nessus provides is: