Best Static Application Security Testing (SAST) Tools
Best static application security testing tools used in 2024 are Coverity static, cxsast, besource, Veracode, and hcl AppScan.



No Cost Personal Advisor
List of 20 Best Static Application Security Testing Tools
Emergents | 2024
Tools by Rogue Wave Software
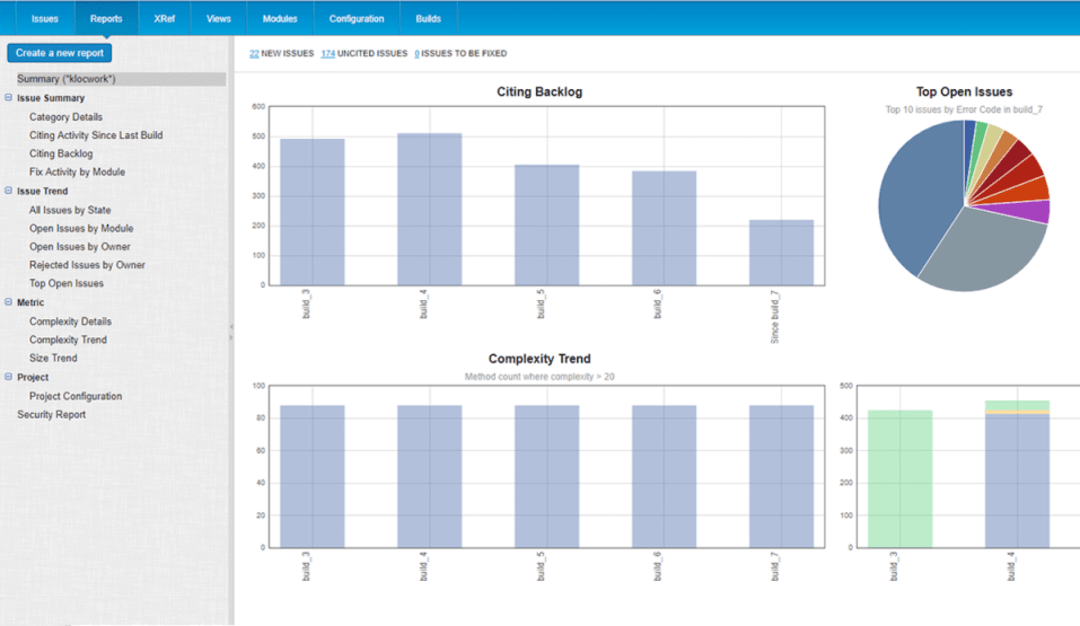
Klocwork is a tool for static application security testing from Perforce. It does static code analysis and SAST for multiple programming languages. Features like Security Vulnerability Identification, Project Streams, Easy Automation, Customizable Dashboard, etc., make coding seamless. It is highly scalable and helps coders to comply with international safety standards easily. Learn more about Klocwork
Explore various Klocwork features, compare the pricing plans, and unlock the potential of seamless operations by selecting the right software for your business.
Features
View all Klocwork Features- Access Controls/Permissions
- Debugging
- Issue Tracking
Klocwork Caters to
- StartUps
- SMBs
- Agencies
- Enterprises
Emergents | 2024
Tools by Checkmarx Ltd
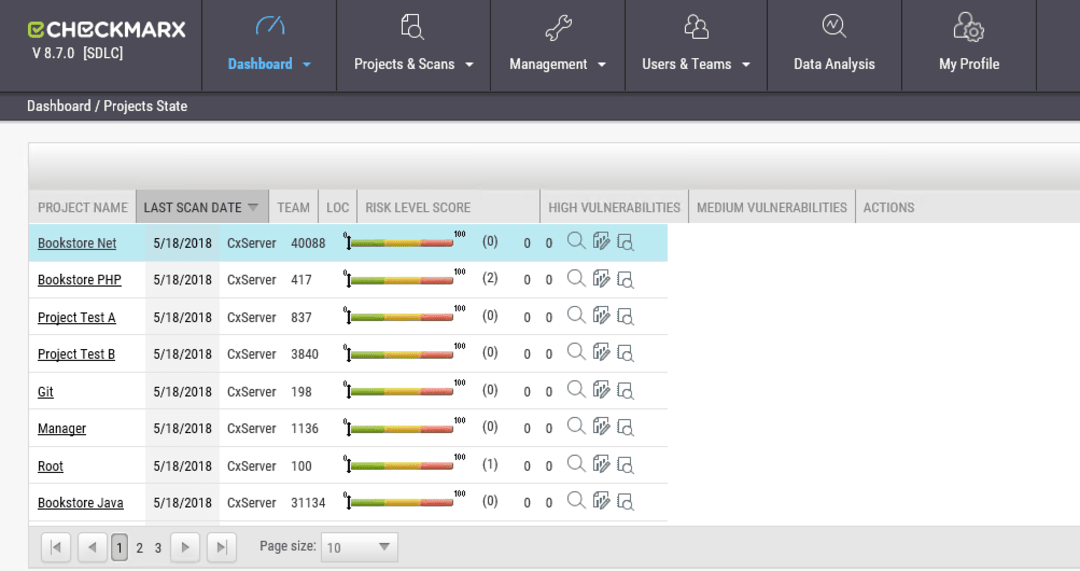
CxSAST is one of the best SAST tools in the market today. A product of Checkmarx Ltd, it is a comprehensive Vulnerability Management Software. This online system provides features like Prioritization, PCI Assessment, and Diagnostic Tools in a single place. It supports dozens of programming languages and is compatible with most programming platforms. Learn more about CxSAST
Explore various CxSAST features, compare the pricing plans, and unlock the potential of seamless operations by selecting the right software for your business.
Features
View all CxSAST Features- PCI Assessment
- Diagnostic Tools
- Prioritization
CxSAST Caters to
- StartUps
- SMBs
- Agencies
- Enterprises
Contenders | 2024
Tools by Veracode
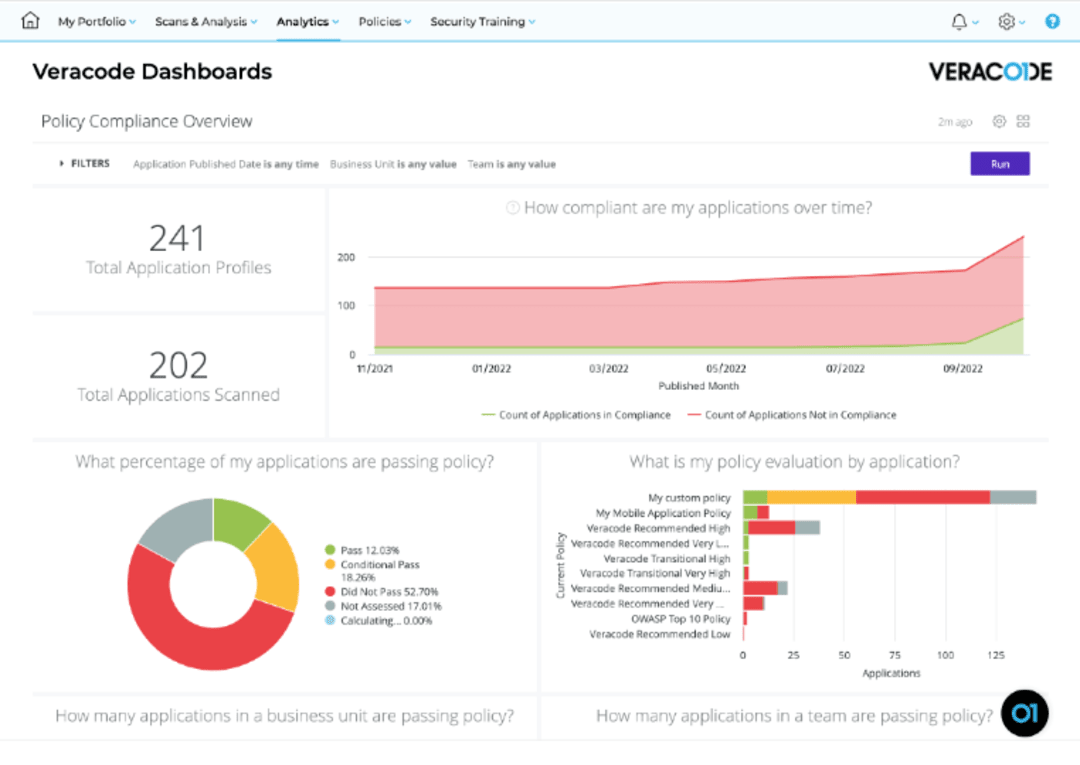
Veracode is one of the most capable static application security testing tools because it can analyze dll, apk (Android apps), and .bca (iOS apps) files equally well. It has excellent Reporting & Analytics, End-to-end Static Scanning, Scalable Cloud Architecture, and Real-time Scan features. Coders can scan 100+ languages and platforms flawlessly with it. Read Veracode Reviews
Explore various Veracode features, compare the pricing plans, and unlock the potential of seamless operations by selecting the right software for your business.
Veracode Caters to
- StartUps
- SMBs
- Agencies
- Enterprises
Contenders | 2024
Tools by GitHub, Inc
A SAST solution that helps to maintain a complete work history, GitHub is used by many industry leaders. Its leading feature is its Version Control System, but it also has other helpful features. Some of these are Backup Systems, Process Management, API Integration, etc. Its open-source community, which facilitates collaboration, is another significant aspect. Read GitHub Reviews
Explore various GitHub features, compare the pricing plans, and unlock the potential of seamless operations by selecting the right software for your business.
Features
View all GitHub Features- Automatic Notifications
- Version Control
- Tracking Features
- History Tracking
- Email Notifications
- Backup System
- Document Storage
- Records Management
Pricing
Personal
$ 7
Per Month
Enterprise
$ 21
Per Month
GitHub Caters to
- StartUps
- SMBs
- Agencies
- Enterprises
Emergents | 2024
Tools by Codacy
Codacy is one of the best open-source SAST tools for efficient source code management. It has features like Distributed Source Control, Code Management, Easy Edit, Collaboration, Advanced Security, etc. Such features make it suitable for freelancers, startups, or large software companies. It is flexible and comes with a visuals-enriched dashboard. Learn more about Codacy
Explore various Codacy features, compare the pricing plans, and unlock the potential of seamless operations by selecting the right software for your business.
Features
View all Codacy Features- Collaboration
- Code Review
- Repository Management
- Bug Tracking
Codacy Caters to
- StartUps
- SMBs
- Agencies
- Enterprises
Contenders | 2024
One-click testing with accurate results
HCL AppScan is an end-to-end security solution for programmers. It provides a comprehensive security network with SAST software, DAST software, Interactive Analysis, and Software Composition Analysis. It has cloud-based, on-premises, and hybrid deployment options, making it highly versatile. Its features include API Testing, Auto Issue Correlation, Cloud Security, Testing Automation, etc. Read HCL AppScan Reviews
Explore various HCL AppScan features, compare the pricing plans, and unlock the potential of seamless operations by selecting the right software for your business.
HCL AppScan Caters to
- StartUps
- SMBs
- Agencies
- Enterprises
Contenders | 2024
Tools by GitLab Inc
Gitlab is a free static application security testing software that supports the entire app development process from planning to execution. It is a collaborative software development platform. It has a large stock of open-source code, built-in comprehensive scanners, including Secret Scanning. Some of its other features include Data Modeling, Deployment Management, Mobile Development, etc. Read GitLab Reviews
Explore various GitLab features, compare the pricing plans, and unlock the potential of seamless operations by selecting the right software for your business.
Features
View all GitLab Features- Data Modeling
- Reporting
- Reporting/Analytics
- Collaboration Tools
- Software Development
- Access Controls/Permissions
- Mobile Development
- Debugging
Pricing
Free
$ 0
User/Month
Bronze
$ 4
User/Month
Silver
$ 19
User/Month
GitLab Caters to
- StartUps
- SMBs
- Agencies
- Enterprises
Emergents | 2024
Tools by Snyk
A platform that allows scanning, prioritizing, and fixing vulnerabilities, Snyk is a comprehensive security management software. SAST tools like Open source, Snyk Code, Snyk Container, Snyk Cloud, and Snyk Infrastructure as Code (IaC) help to fix misconfigurations. It also offers Vulnerability Assessment, Patch Management, Asset Discovery, Risk Management, and other features. Learn more about Snyk
Explore various Snyk features, compare the pricing plans, and unlock the potential of seamless operations by selecting the right software for your business.
Features
View all Snyk Features- Risk Management
- Asset Tagging
- Vulnerability Assessment
- Prioritization
- Asset Discovery
- Patch Management
- Policy Management
- Vulnerability Scanning
Pricing
Free
$ 0
Per Month
Standard
$ 599
Per Month
Pro
$ 1659
Per Month
Snyk Caters to
- StartUps
- SMBs
- Agencies
- Enterprises
Contenders | 2024
Tools by Synopsys, Inc
Coverity is a fast, accurate, and scalable static analysis SAST Solution. It lets development and security teams manage quality and security issues early in the software’s lifecycle. With features like API Lifecycle Management, Approval Process Control, Deployment Management, Parallel Analysis, etc., it works for startups, SMEs, or enterprises. Read Coverity Static Reviews
Explore various Coverity Static features, compare the pricing plans, and unlock the potential of seamless operations by selecting the right software for your business.
Features
View all Coverity Static Features- Approval Process Control
- Reporting/Analytics
- Collaboration
- Mobile Development
- Contact Management
- Software Development
- Dashboard
- Deployment Management
Coverity Static Caters to
- StartUps
- SMBs
- Agencies
- Enterprises
Emergents | 2024
Tools by SonarSource
SonarQube is one of the best open-source SAST tools for continuously inspecting code quality. It provides easy project onboarding with integration to GitLab, Azure, GitHub, etc. It offers 5000+ coding rules and supports Java, C#, Python, etc. It also synchronizes with SonarLint to ensure standardized rules and analysis settings. Learn more about SonarQube
Explore various SonarQube features, compare the pricing plans, and unlock the potential of seamless operations by selecting the right software for your business.
SonarQube Caters to
- StartUps
- SMBs
- Agencies
- Enterprises
Emergents | 2024
Tools by GitGuardian
GitGuardian is a code security platform that supports collaboration between developers, security teams, and cloud operations. It offers multiple SAST tools like Incident Management, Database Security Audit, Vulnerability Scanning, Whitelisting / Blacklisting, Automated Secrets Detection, and GitGuardian Public and Internal Monitoring. It supports the security of the whole software development lifecycle. Learn more about GitGuardian
Explore various GitGuardian features, compare the pricing plans, and unlock the potential of seamless operations by selecting the right software for your business.
Features
View all GitGuardian Features- Vulnerability Protection
- Activity Log
- Patch Management
- File Access Control
- User Activity Monitoring
- Whitelisting / Blacklisting
- Incident Management
- Database Security Audit
GitGuardian Caters to
- StartUps
- SMBs
- Agencies
- Enterprises
Contenders | 2024
Worlds most powerful mobile security tool
The static application security testing software Appknox is a powerful plug-and-play mobile app security solution. It is used to detect threats in apps within minutes. It can complete security testing within 90 minutes with coverage that includes client-side and server-side security testing. Its features include SAST, DAST, API Testing, and Manual Penetration Testing. Read Appknox Reviews
Explore various Appknox features, compare the pricing plans, and unlock the potential of seamless operations by selecting the right software for your business.
Appknox Caters to
- StartUps
- SMBs
- Agencies
- Enterprises
Emergents | 2024
Automate code reviews with static analysis
DeepSource is one of the best free SAST tools for freelancers and new businesses. It has 16+ static analyzers to support all modern technologies. It supports multiple programming languages and has features like Bug Tracking, Build Automation, Code Review, etc. It improves security efficiency by automating the finding and fixing of issues. Learn more about DeepSource
Explore various DeepSource features, compare the pricing plans, and unlock the potential of seamless operations by selecting the right software for your business.
Features
View all DeepSource Features- Code Review
- Bug Tracking
- Build Automation
- Collaboration
- Access Controls/Permissions
Pricing
FREE - For small teams
$ 0
3 Users
PRO - For solo developers
$ 12
Single User
TEAM - For growing teams
$ 24
Full Licence
DeepSource Caters to
- StartUps
- SMBs
- Agencies
- Enterprises
Emergents | 2024
Embedding security as a service
Micro Focus is a static application security testing service that supports both legacy and modern technologies. It is an end-to-end platform that offers SAST, DAST, IAST, MAST, and SCA as a service. It also has wide-ranging integrations. Features like Application Delivery, Application Modernization, CyberRes, etc., ensure that their clients include industry leaders. Learn more about Micro Focus Fortify
Explore various Micro Focus Fortify features, compare the pricing plans, and unlock the potential of seamless operations by selecting the right software for your business.
Micro Focus Fortify Caters to
- StartUps
- SMBs
- Agencies
- Enterprises
Emergents | 2024
Tools by StackHawk Inc.
StackHawk is a SAST software that helps developers fix security issues before hitting production. It supports them in finding, triaging, and resolving security concerns in their applications. Features like Automated Security Testing, Pre-production API, and Web Application Security Testing make it a popular security tool. It is also an API security testing mechanism. Learn more about StackHawk
Explore various StackHawk features, compare the pricing plans, and unlock the potential of seamless operations by selecting the right software for your business.
StackHawk Caters to
- StartUps
- SMBs
- Agencies
- Enterprises
Emergents | 2024
Tools by CAST
CAST AIP is a fully-featured static application security testing tool for SMEs, Enterprises, and Agencies. It offers dashboards, integrates with IDEs, and automates tests in a single place. It helps businesses raise their software’s security level by protecting against breaches, outages, corruption of data, and external catastrophes. Learn more about CAST Application Intelligence Platform
Explore various CAST Application Intelligence Platform features, compare the pricing plans, and unlock the potential of seamless operations by selecting the right software for your business.
CAST Application Intelligence Platform Caters to
- StartUps
- SMBs
- Agencies
- Enterprises
Emergents | 2024
Secure and manage open source components
WhiteSource, currently known as Mend.io, is one of the SAST tools focused on open-source components of programming and license compliance management. Features like Remediation, Prioritization, Vulnerability Management, Security Advisories, Vulnerability Knowledge Bases, and Real-Time Reporting & Dashboards help quickly resolve security issues. It even supports 200+ languages. Learn more about WhiteSource
Explore various WhiteSource features, compare the pricing plans, and unlock the potential of seamless operations by selecting the right software for your business.
Features
View all WhiteSource Features- Vulnerability Scanning
- Remediation
- Policy Management
- Real-Time Reporting & Dashboards
- Vulnerability Protection
- Prioritization
- Vulnerability Management
- Vulnerability Assessment
WhiteSource Caters to
- StartUps
- SMBs
- Agencies
- Enterprises
Emergents | 2024
Static Application Security Testing (SAST)
Features like Ticket Management, Issue Tracking, Backlog Management, Release Management, etc., make PVS-Studio an excellent static application security testing tool. It supports multiple programming languages. And it runs on Windows, Linux, and macOS operating systems. It is an analyzer that detects errors- typos, dead code, and potential vulnerabilities in the development lifecycle. Learn more about PVS-Studio
Explore various PVS-Studio features, compare the pricing plans, and unlock the potential of seamless operations by selecting the right software for your business.
Features
View all PVS-Studio Features- Filtering
- Ticket Management
- Issue Tracking
- Task Management
- Workflow Management
- Backlog Management
- Release Management
PVS-Studio Caters to
- StartUps
- SMBs
- Agencies
- Enterprises
Emergents | 2024
Tools by WhiteHat Security, Inc
Sentinel Source is a static application security testing system that provides end-to-end solutions to programmers. Features like Code Analysis, Dashboards, and Integrated IDEs allow businesses to quickly deploy a scalable app security program. It can scan open-source codes and custom-built applications and offers three levels of testing. Learn more about Whitehat Sentinel Source
Explore various Whitehat Sentinel Source features, compare the pricing plans, and unlock the potential of seamless operations by selecting the right software for your business.
Whitehat Sentinel Source Caters to
- StartUps
- SMBs
- Agencies
- Enterprises
Emergents | 2024
Security Solutions For Your DevOps Process.
Kiuwan is an all-encompassing SAST software application and web application security tool. Its end-to-end security platform empowers the development process by combining SAST, SCA, and QA. It gives a real-time view of the software portfolio security status, making the application bulletproof. It also offers Risk Management, Vulnerability Scanning, Compliance Reporting, and several integrations. Learn more about Kiuwan Code Security
Explore various Kiuwan Code Security features, compare the pricing plans, and unlock the potential of seamless operations by selecting the right software for your business.
- Vulnerability Assessment
- Compliance Reporting
- Risk Management
- Vulnerability Scanning
- Vulnerability Management
Kiuwan Code Security Caters to
- StartUps
- SMBs
- Agencies
- Enterprises
Are you an individual who develops software or a security expert searching for the finest SAST tools to guarantee the security of your software program? It has become critical to recognize vulnerabilities and rectify them before deployment due to the growing number of cyberattacks and data breaches.
SAST instruments assist you in identifying security weaknesses in the code during the development phase, allowing you to address concerns before they pose a risk. In this purchasing guide, we will examine the leading SAST instruments on the market, including their characteristics, advantages, and drawbacks, to assist you in making an informed selection and selecting the appropriate tool for your software security requirements.
What are Static Application Security Testing (SAST) Tools?
SAST, or Static Application Security Testing, is a vital security tool that plays a crucial role in the Software Development Life Cycle (SDLC) environment. Its primary function is to pinpoint security flaws in enterprise applications by analyzing the source code before it is compiled.
SAST is a type of testing that involves scanning the application code in a meticulous manner to uncover any potential security weaknesses. This method empowers developers to address any identified security concerns and re-evaluate the application before it is released to the production environment.
By facilitating early detection and remediation of security vulnerabilities in the SDLC, SAST helps organizations secure their applications effectively. When integrated into a Continuous Integration/Continuous Deployment (CI/CD) pipeline, SAST transforms DevOps into DevSecOps, promoting a secure and agile development environment.
How does SAST Tool Work?
Static application security testing tools employ a process of examining the code to identify any coding design flaws that may lead to an application vulnerability. It can detect various security concerns such as mishandled input, SQL injections, and error handling, among others.
This security tool can identify security and functional issues in the code, and it can enforce coding standards for the development team. It is advisable to incorporate Static Application Security Testing at the beginning of a project rather than waiting until the codebase becomes too large.
This is because it could pose a challenge for the development and security teams to remediate the vulnerabilities. SAST and DAST are often compared, but they differ in many ways.
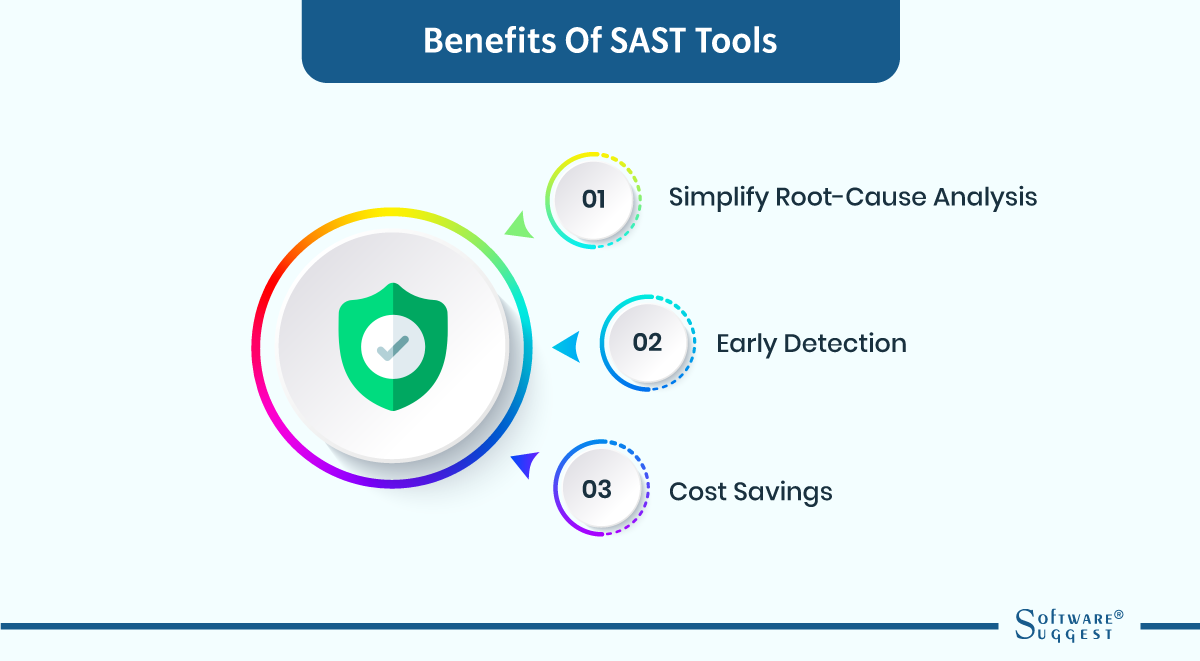
Benefits of SAST Tools
SAST is a process of analyzing computer software without actually running the software. The source code of an app is examined with SAST solutions to identify any security weaknesses. The inclusion of SAST in the Software Development Life Cycle (SDLC) yields multiple advantages.
-
Simplify root-cause analysis
Root-cause analysis is made easier by SAST tools, which is one of its main perks. It is simpler to pinpoint the underlying cause of a security issue when using SAST tools, which can find vulnerabilities in an application's source code. This is so because SAST tools offer thorough details on where the code vulnerability is located. The issue's root cause can be swiftly determined and fixed with this information.
-
Early detection
Another perk of SAST tools is their ability to detect vulnerabilities at an early stage. SAST tools can identify weaknesses during the design phase of the SDLC when they are relatively simple to address. This helps to shift security testing to the left, which is a critical practice in software development. Early identification of vulnerabilities can prevent security problems from arising in the later stages of the SDLC.
-
Cost savings
SAST solution can be employed alongside a Dynamic Application Security Testing (DAST) instrument. SAST instruments are more rapid and budget-friendly than DAST instruments. SAST instruments can detect security flaws in the source code, whereas DAST instruments mandate the application to be functional. By identifying security flaws in the initial stages of the development process, SAST instruments can economize time and money. These tools can do it by lessening the requirement for costly rectification endeavors in the later stages of the development phase.
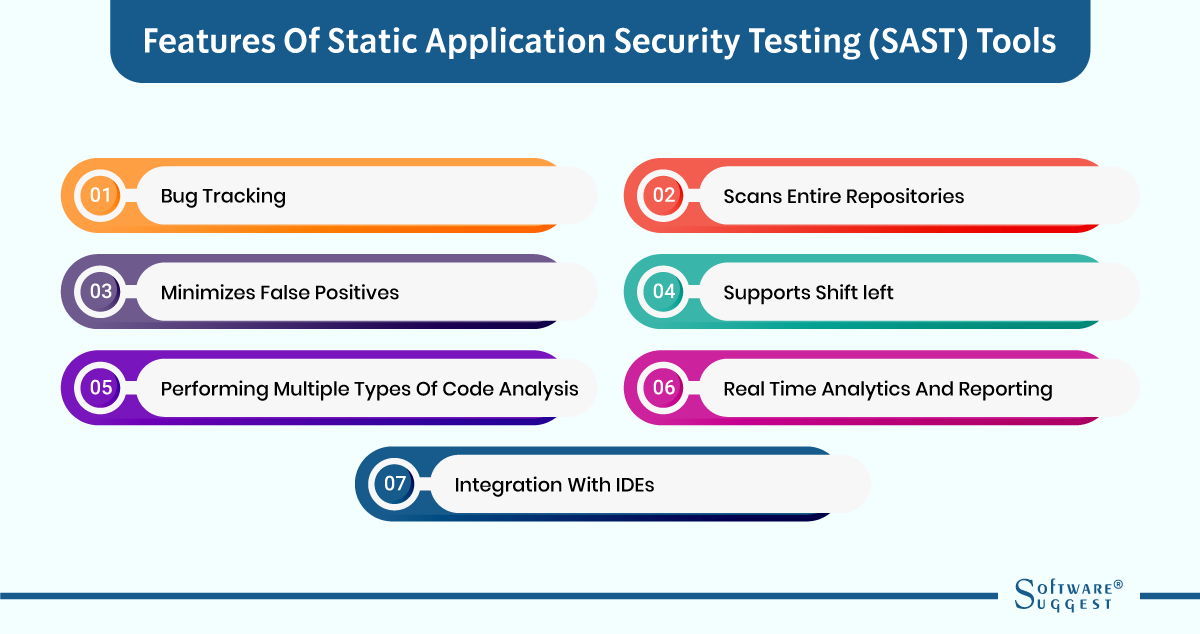
Features of Static Application Security Testing (SAST) Tools
Did you know that every phase of the software development lifecycle includes open source SAST tools? This is so that security problems in the code can be found before the program is released.
This Static application security testing software examines an app's source code to find plausible security issues. Now we will know the seven common features of SAST tools that you should check for when purchasing one.
-
Bug tracking
Bug tracking is among the most significant aspects of SAST tools. SAST tools can recognize potential security flaws in the source code of an application and equip developers with comprehensive details about the matter. This information encompasses the position of the flaw in the code, its type, and its severity. Such information is crucial for developers to address the issue promptly and effectively.
Moreover, SAST tools can monitor the progress of bugs and vulnerabilities. It implies that developers can monitor the fixes made and the ones that still need attention. This characteristic is essential for extensive development groups, where multiple programmers might be operating on identical source code. Bug tracking ensures that everyone is informed about the status of each bug and can collaborate to remedy them.
-
Scans entire repositories
Another significant characteristic of SAST software is its ability to inspect complete repositories. This implies that SAST tools can scrutinize all the code in a project rather than just individual files. This is crucial because security flaws can exist across multiple files and components of an application. By inspecting complete repositories, SAST tools can detect potential security concerns that may have been overlooked during manual code reviews.
Examining complete repositories also aids developers in identifying security issues in third-party libraries and dependencies. Numerous applications depend on third-party libraries and dependencies, which may introduce security vulnerabilities to an application. SAST tools can discover these vulnerabilities and provide developers with guidance on how to address them.
-
Minimizes false positives
One of the obstacles in utilizing Static application security testing tools is the likelihood of incorrect identifications. These occur when SAST tools pinpoint a possible security threat that is actually not a threat. This can cause annoyance among developers as it results in unproductive time and energy.
Nevertheless, several SAST tools incorporate functions that mitigate false positives. For instance, certain SAST tools employ machine learning algorithms to scrutinize code and recognize potential threats. These algorithms can learn from past scans and enhance their precision gradually.
-
Supports shift left
In software development, SAST tools play a significant role in the shift left approach. This methodology prioritizes the detection and resolution of issues at the early stages of development. Security Application and Software Testing (SAST) tools assist programmers and developers in detecting and rectifying shortcomings in security prior to the deployment of the code to the production environment.
SAST software are seamlessly integrated into the development process, designed to work well with IDEs like Eclipse and Visual Studio. SAST solution enables developers to locate and repair vulnerabilities while writing code. It also reduces the time and effort required to address them later in the development cycle.
-
Performing multiple types of code analysis
SAST technology is capable of performing a variety of code analyses. It scans the programming and software architecture of an application to identify vulnerabilities related to security. Additionally, SAST solutions can scrutinize code to detect violations of coding standards, performance issues, and other defects that may impact the code's quality.
By performing multiple types of code analysis, SAST software provides developers with a comprehensive view of their code. This ensures that the code is secure, effective, efficient, and adheres to coding standards.
-
Real-time analytics and reporting
SAST software offers instant analysis and reporting, a crucial aspect for developers. The instant analysis enables developers to view the outcomes of their code analysis while coding, which aids in detecting vulnerabilities at an early stage of development. This, in turn, makes it simpler and less expensive to rectify them.
Reporting is another vital feature of SAST tools. They generate comprehensive reports that specify the identified vulnerabilities, their level of severity, and their position in the code. Developers can use this information to prioritize and eradicate vulnerabilities.
-
Integration with IDEs
The incorporation of IDEs is a crucial aspect of SAST tools. IDEs, which are software applications that offer developers a comprehensive platform for coding and testing, are vital. With the integration of IDEs, SAST tools can offer developers prompt feedback on security loopholes while they are writing code.
There are several methods of integrating SAST tools with IDEs. For instance, some SAST tools offer IDE plugins that permit developers to execute security scans directly from the IDE. This enables developers to detect and resolve vulnerabilities while writing code, lessening the time and energy required to rectify them later in the development process.
Static Application Security Testing ( SAST): Pros and Cons
SAST is a form of security testing that examines the source code or compiled form of an application to locate probable security flaws. Developers widely use SAST to boost the security of their software applications. Nonetheless, SAST also has its own set of benefits and drawbacks, just like any other testing technique. Now we will examine the advantages and disadvantages of SAST.
Pros
|
Pros of SAST |
Explanation |
|
Early Detection of Vulnerabilities |
SAST has the capacity to identify vulnerabilities in the application's source code or compiled version during the development phase, allowing programmers to fix them before release. |
|
Comprehensive Testing |
SAST is capable of identifying a wide variety of security flaws, including those that are code-level flaws like buffer overflows, SQL injection, and cross-site scripting (XSS). |
|
Faster Testing |
SAST is an automated testing technique that can examine an application's source code or compiled version considerably more quickly than manual testing, which can cut down on testing time and effort. |
|
Cost-Effective |
SAST can help organizations save money by lowering the cost of resolving vulnerabilities later in the software development life cycle by discovering them early in the development cycle. |
Cons
|
Cons of SAST |
Explanation |
|
False Positives |
SAST software may generate erroneous alarms, signaling the presence of a security loophole that is not actually there. This can lead to developers wasting time and energy verifying each find manually. |
|
Limited Scope |
SAST is limited to scanning the source code or compiled version of the application and cannot identify vulnerabilities in the underlying infrastructure, such as the operating system, network, or database. |
|
Incomplete Coverage |
SAST might overlook security loopholes that are not code-related, such as misconfiguration or authentication and access control issues. |
|
Requires Expertise |
Effective use of SAST necessitates expertise in coding and security testing. Developers must be properly trained to employ the tools and accurately interpret the results. |
How to Choose the Right Static Application Security Testing (SAST) Tools?
Selecting the appropriate Static application security testing tools is crucial to guarantee the safeguarding of your software applications. The market provides numerous alternatives, which can be daunting when it comes to making a choice. Now we will elaborate on the essential aspects to contemplate while selecting a SAST tool.
-
User interface (UI)
The usability of a SAST tool largely depends on its user interface. A well-designed UI should be intuitive, easy to use, and enable smooth navigation. It should generate the results in a clear and concise manner. Additionally, the UI should offer options for users to personalize the testing parameters according to their requirements.
-
Multi-language support
SAST tools must be able to support many programming languages in order to be useful in discovering vulnerabilities across distinct apps. They should be capable of efficiently discovering security problems by scanning and analyzing source code published in a variety of languages.
-
Usability
When selecting Open source SAST tools, usability is a vital factor to consider. The program must be easy to install, configure, and establish. Furthermore, it should have a user-friendly interface that requires no technical expertise. The tool should integrate effortlessly into the developer's workflow.
-
Accuracy
To effectively identify weaknesses, accuracy is if highest significance for a SAST tool. The tool must have a high level of accuracy in detecting security weaknesses, reducing the number of false positives and false negatives. Precision is very essential to avoid wasting time and resources investigating possible weaknesses.
-
Scalability
The ability of a SAST tool to adapt to the requirements of various businesses is crucial, from modest startups to extensive corporations. The tool must have the capacity to process significant quantities of source code without any drop in performance. Additionally, it should facilitate scanning distribution, allowing multiple users to scan code concurrently.
-
Scanning speed
Particularly in extensive codebases, the scanning rate of a SAST tool is a crucial consideration. The tool must scan code rapidly and effectively without compromising the precision of the outcomes. A tool that takes an extended period to scan code can lead to delays in the development process.
-
Vulnerability identification
It is necessary for the SAST tool to possess the capability of detecting various vulnerabilities, comprising but not limited to SQL injection, cross-site scripting (XSS), and buffer overflows. Additionally, the tool should be competent in identifying vulnerabilities that are exclusive to the programming language or framework utilized.
-
Reverse engineer binaries
A SAST tool's worth is amplified when it can perform the function of reverse engineering binaries. The ability to analyze compiled code provides further discernment into probable vulnerabilities that may remain concealed in the source code. This trait proves especially advantageous when examining third-party libraries and dependencies.
-
Value for money
Ultimately, the cost-effectiveness of a SAST tool is a pivotal aspect to take into account. The price of the tool ought to align with the financial plan of the company, and the functionalities presented should validate the expenditure. The tool must yield a favorable return on investment by spotting susceptibilities at the beginning of the development phase, thus curbing the expense of rectifying them in the future.
Top 5 Static Application Security Testing (SAST) Tools
|
Name
|
Free Trial
|
Demo
|
Starting Price
|
|---|---|---|---|
| No |
No |
Contact sales for pricing | |
|
SpectralOps |
14 days |
Yes | $5/user/month |
|
Checkmarx |
No |
No |
Contact sales for pricing |
| No |
Yes |
Contact sales for pricing | |
|
Reshift |
14 days |
Yes |
$2/user/month |
With the above-guiding points mentioned, it is clear that you have a referring point when you choose static application security testing tools.
But even if you have the knowledge for it, it’s very confusing to choose the best software in the market. We’ve made it easy for you. Here are the top 5 static application security testing (SAST) Tools that you can consider using in your company.
-
Klocwork

For C++, C#, JavaScript, Java, Python, and Kotlin, Klocwork is a SAST tool. It is plausible to identify problems with software reliability, security, and quality. It can be applied to guarantee standard compliance.This static analyzer can sustain the development pace while enforcing regular compliance for security and quality. It also offers control, collaboration, and reporting tools for the entire company.
Features
- Offers in-depth static code analysis for C, C++, C#, and Java languages
- Provides real-time feedback and guidance for developers
- Supports integration with popular IDEs and builds systems
- Offers flexible deployment options, including cloud and on-premise
- Offers comprehensive reporting and tracking of code quality metrics
Pros
- No User Configuration needed
- Easy to Use
- It is a very interactive application security testing tool
- Proper secure code
- Connected desktop extensions offer instant distinct examination outcomes within integrated development environments
Cons
- Can produce a high volume of false positives
-
SpectralOps

SpectralOps is a SAST tool. Unlike traditional solutions that attempt to mimic humans, SpectralOps strives to think like them and write as they would — using natural language processing and artificial intelligence.By leveraging advanced technologies such as these, businesses can create experiences tailored specifically to their customers while ensuring accuracy and authenticity every time. With an expansive suite of features designed around user experience optimization, it's never been easier for users to craft content with both speed and precision.
Features
- Monitor out-of-sight assets
- Shift-left log shipping integration
- Can install your build systems plugin
- Has custom hooks to automate early issue detection
Pros
- Helps in mitigating risks
- Over 2000 detectors keep your firm safe
- Takes a few seconds to scan
Cons
- Few may find it a little difficult to use
-
Checkmarx

Checkmarx is a software analysis tool that provides developers with immediate feedback on probable security vulnerabilities. It is adaptable to various programming languages and can be merged with commonly used development software. The primary objective of Checkmarx is to assist organizations in identifying and resolving security issues early in the software development lifecycle.Feature
- Static application security testing
- SaaS or on-premises deployment options
- Continuous scanning and monitoring
- Integration with popular DevOps tools
- Comprehensive vulnerability management
Pros
- Provides accurate and reliable scanning of code
- Provides real-time feedback to developers
- Offers flexible deployment options
Cons
- Have the tendency to can produce a high volume of false positives
- UI might be difficult
-
Veracode

Veracode is a cloud-native application security platform that offers SAST, DAST, and SCA capabilities. It has numerous integrations with commonly used development tools and provides comprehensive reports and analytics to help establishments manage their software security. It aims to help organizations minimize their overall risk of cyber attacks.Feature
- Flexible policy management
- Security Integrated into The SDLC
- A security level configuration can be set for flaws
- Had e-learning facility
Pros
- Provides detailed report
- Meticulous scanning
- Easy to use
Cons
- Reports can be easier to read
-
Reshift

Reshift is an establishment that sells solutions for evaluating and transforming code that works with plenty of programming languages. It utilizes a rule-based methodology to find possible issues in code and, practically, offers automated fixes. It was made to assist programmers in improving the overall standard of their code while lowering the likelihood of flaws.Features
- Security assessment solutions for web applications, mobile applications, and APIs
- Qualified and certified security testers with extensive experience
- Tailor-made testing strategies that suit the customer's requirements
- Elaborate reporting with practical suggestions
- Constant support and remediation assistance
Pros
- Delivers extensive testing for various digital assets
- Offers adaptable testing strategies that are customized for each business
- Employs proficient security testers who possess certifications
- Provides detailed reporting with valuable recommendations to enhance security
Cons
- Pricing information is not readily available on the website and may differ based on individual requirements
- Not one of the free SAST tools
- Certain clients may prefer to conduct in-house testing rather than outsourcing to an external service
Pricing
Pricing is based on individual requests.
How to Implement SAST Tools?
Utilizing Static Application Security Testing (SAST) instruments can notably enhance the safety of your software applications. Nonetheless, executing them can be a difficult task. Below are essential stages to aid you in efficiently putting into effect SAST tools.
-
Find the right tool
The initial step in executing SAST instruments is to identify the appropriate tool for your software security requirements. There are several SAST instruments accessible in the market, each with its distinctive characteristics and capabilities. You must contemplate factors such as the programming languages you employ, the magnitude of your codebase, and the variety of susceptibilities you wish to discover.
Some of the most widespread SAST instruments comprise Veracode, Checkmarx, Fortify, and SonarQube. Each instrument has its own advantages and restrictions. For instance, Veracode is recognized for its user-friendliness, whereas Checkmarx is renowned for its proficiency in detecting intricate susceptibilities.
-
Set up testing & deployment
After choosing the appropriate SAST software, it is necessary to establish testing and deployment protocols. Generally, SAST software mandates that you transfer your codebase to a cloud-based platform, where it is scrutinized for susceptibilities. It is imperative to guarantee that your codebase is suitably arranged and fulfills the tool's conditions.
Prior to initiating the scan, it is advisable to personalize the tool to meet your individual requirements. This involves configuring the scan parameters, such as the categories of susceptibilities you wish to identify, the level of severity of those susceptibilities, and the frequency of the scans.
-
Weed out false positives
One of the challenges faced when using the SAST solution is the high occurrence of incorrect positives. These refer to instances where the tool flags weaknesses that do not actually exist. It can be problematic as it leads to the expenditure of resources in trying to address non-existent issues.
To resolve this issue, this software thoroughly analyzes the scan results. It involves scrutinizing each problem identified by the tool and determining whether it is a genuine vulnerability or an incorrect positive. Additionally, to lessen the frequency of incorrect positives, it is vital to ensure that the tool's logic and configurations are appropriately calibrated.
-
SAST tool customization
The adaptability of SAST tools is quite extensive, enabling you to personalize them according to your particular requirements. As an illustration, you can set up the tool to spot certain kinds of susceptibilities, like SQL injection or cross-site scripting. Additionally, you can modify the intensity levels of the susceptibilities identified by the tool.
Personalization necessitates a comprehensive comprehension of the tool's potential and constraints. It is advisable to refer to the tool's documentation and request guidance from the tool's support team to confirm that you are customizing the tool accurately.
-
Incorporate in your CI pipeline
To optimize the advantages of SAST tools, it is advisable to integrate them into your continuous integration (CI) pipeline. CI is a software development approach where modifications to the code are frequently combined into a shared repository and automatically tested.
By integrating SAST tools into your CI pipeline, you can identify vulnerabilities in the early stages of development when they are more manageable and cost-effective to rectify.
To integrate SAST tools into your CI pipeline, automating the scanning process and incorporating it into your build and deployment procedures is essential. Moreover, you should ensure that the scan outcomes of the tool are automatically communicated to developers so that they can promptly address any identified issues.
-
Training
Ultimately, it is crucial to furnish developers with adequate instruction on the proficient utilization of SAST tools. These tools can be intricate and necessitate a comprehensive comprehension of security susceptibilities and programming languages. Developers must comprehend how to construe the outcomes of the tool, prioritize problems, and competently rectify vulnerabilities.
Education can come in diverse forms, including workshops, web-based courses, or individualized sessions. It is vital to ensure that the training is continual and encompasses both the tool's operation and optimal techniques for secure coding.
How are SAST Tools Different from DAST Tools?
Two frequently utilized tools are SAST and DAST tools. Even though both are intended to recognize and forestall security weaknesses, they contrast in their methodology and the categories of weaknesses they identify.
|
SAST |
DAST |
|
|
Conclusion
To sum up, it is essential to take into account the distinct demands of your project when selecting a SAST solution. SAST solutions are a valuable asset for developers who aim to ensure the safety of their codebase, although they may generate imprecise outcomes and overlook certain vulnerabilities.
SAST tools can economize time and resources by identifying vulnerabilities at an early stage; hence, they may not always be more expensive in terms of the expenses linked to remedying vulnerabilities. The development procedure may incorporate SAST testing or the utilization of an automated solution. It is vital to bear in mind that SAST technologies function optimally when employed in the initial phases of the software development process.
FAQs
Not necessarily. By identifying vulnerabilities early in the development cycle, SAST technologies can save time and dollars.
Automated SAST software testing can be performed using certain tools or by incorporating SAST into the development process. It is crucial to bear in mind that SAST tools are most effective when employed during the software development stage of the software life cycle to detect and rectify defects prior to their release to the general public.



















.png)