Best Vulnerability Assessment Tools
Best available vulnerability assessment tools, include manager plus, comodo, retina network security scanner, appknox, openvas, etc.



No Cost Personal Advisor
List of 20 Best Vulnerability Assessment Tools
Emergents | 2024
All-in-One Vulnerability Management Tool
Vulnerability Manager Plus is a comprehensive and strategic vulnerability assessment solution built for security teams. It helps you gain complete visibility of processes, address threats by offering built-in patch management functionality. Learn more about Vulnerability Manager Plus
Explore various Vulnerability Manager Plus features, compare the pricing plans, and unlock the potential of seamless operations by selecting the right software for your business.
- Vulnerability Scanning
- Vulnerability Assessment
- Vulnerability Protection
- Policy Management
- Network Scanning
- Risk Management
- Patch Management
- Prioritization
Vulnerability Manager Plus Caters to
- StartUps
- SMBs
- Agencies
- Enterprises
Emergents | 2024
Tools by Acunetix
Netsparker Security Scanner is a fully featured security Vulnerability Assessment Tool designed to serve Agencies, Startups. Netsparker Security Scanner provides end-to-end solutions designed for Web App. This online Vulnerability Management system offers Vulnerability Assessment, Vulnerability Protection, IOC Verification, Risk Management, Real Time Monitoring at one place. Learn more about Netsparker
Explore various Netsparker features, compare the pricing plans, and unlock the potential of seamless operations by selecting the right software for your business.
Features
View all Netsparker Features- Database Security Audit
- Prioritization
- Asset Discovery
- Real Time Monitoring
- Vulnerability Protection
- Web Scanning
- Vulnerability Scanning
- IOC Verification
Netsparker Caters to
- StartUps
- SMBs
- Agencies
- Enterprises
Emergents | 2024
Tools by Greenbone Networks GmbH
OpenVAS is a fully featured and Best Vulnerability Assessment Tool designed to serve Agencies, Enterprises. OpenVAS provides end-to-end solutions designed for Windows. This online Vulnerability Management system offers Prioritization, Asset Tagging, Web Scanning, Asset Discovery, Risk Management at one place. Learn more about OpenVAS
Explore various OpenVAS features, compare the pricing plans, and unlock the potential of seamless operations by selecting the right software for your business.
Features
View all OpenVAS Features- Vulnerability Assessment
- Asset Discovery
- Asset Tagging
- Web Scanning
- Network Scanning
- Prioritization
- Risk Management
OpenVAS Caters to
- StartUps
- SMBs
- Agencies
- Enterprises
Emergents | 2024
Tools by Acunetix
Acunetix is a fully featured Vulnerability Testing Tool designed to serve Agencies, SMEs. Acunetix provides end-to-end solutions designed for Windows. This online Cyber Security system offers Database Security Audit, Risk Management, Web Threat Management, Asset Tagging, Audit Trail at one place. Learn more about Acunetix
Explore various Acunetix features, compare the pricing plans, and unlock the potential of seamless operations by selecting the right software for your business.
Features
View all Acunetix Features- Risk Management
- Compliance Management
- Vulnerability Assessment
- Audit Trail
- File Access Control
- Vulnerability Protection
- Web Threat Management
- Network Scanning
Acunetix Caters to
- StartUps
- SMBs
- Agencies
- Enterprises
Contenders | 2024
Tools by Nmap
Nmap is a fully featured Network Mapping Software designed to serve Startups, Agencies. Nmap provides end-to-end solutions designed for Web App. This online Network Mapping system offers Color Codes/Icons at one place. Read Nmap Reviews
Explore various Nmap features, compare the pricing plans, and unlock the potential of seamless operations by selecting the right software for your business.
Features
View all Nmap Features- Color Codes/Icons
Nmap Caters to
- StartUps
- SMBs
- Agencies
- Enterprises
Emergents | 2024
Tools by Comodo
Comodo's free vulnerability testing tool that provides the best protection from malware instances, virus infection, and suspicious hidden files. It is a reliable, cloud-based protection that scans quickly and updates continuously to include the latest malware information from around the globe. Read Comodo Reviews
Explore various Comodo features, compare the pricing plans, and unlock the potential of seamless operations by selecting the right software for your business.
Features
View all Comodo Features- Detect viruses
- Multilingual Support
- Longer Graph History
- Advanced Firewall
- Network Monitoring
- Internet Security
- Basic Firewall
- Identity Protection
Comodo Caters to
- StartUps
- SMBs
- Agencies
- Enterprises
Contenders | 2024
Worlds most powerful mobile security tool
Appknox automated scanner is easy to use vulnerability testing tool and has vast API compatibilities which make it simple to integrate into the mobile Application Development cycle, providing complete automation of SAST, DAST, and Application Program Interface(API) Testing. Read Appknox Reviews
Explore various Appknox features, compare the pricing plans, and unlock the potential of seamless operations by selecting the right software for your business.
Appknox Caters to
- StartUps
- SMBs
- Agencies
- Enterprises
Contenders | 2024
Fastest and most accurate automated vulnerability
SanerNow offers a fully integrated vulnerability assessment tool with patch remediation from the same console. Leveraging the world’s largest vulnerability database with 100,000+ checks, SanerNow effectively detects vulnerabilities and remediates them instantly. Read SecPod's SanerNow Vulnerability Management Reviews
Explore various SecPod's SanerNow Vulnerability Management features, compare the pricing plans, and unlock the potential of seamless operations by selecting the right software for your business.
- Maintenance Scheduling
- Vulnerability Management
- Whitelisting / Blacklisting
- Vulnerability Scanning
- Vulnerability Assessment
- Real Time Monitoring
- Database Security Audit
- Risk Management
SecPod's SanerNow Vulnerability Management Caters to
- StartUps
- SMBs
- Agencies
- Enterprises
Contenders | 2024
Tools by SolarWinds Worldwide LLC.
SolarWinds is a database software that includes remote access, asset tracking, backup, and monitoring. This DBMS has a nice user interface. It database system is trusted by a lot of users to create, retrieve, update and manage their data. Read SolarWinds Reviews
Explore various SolarWinds features, compare the pricing plans, and unlock the potential of seamless operations by selecting the right software for your business.
Features
View all SolarWinds Features- Email Monitoring
- Backup Log
- Scheduling
- Real Time Monitoring
- CPU Monitoring
- Database Servers
- Analytics
- Uptime Monitoring
Pricing
Starter
$ 2995
Onetime
SolarWinds Caters to
- StartUps
- SMBs
- Agencies
- Enterprises
Contenders | 2024
Tools by Tenable Network Security
Nessus is a fully featured Vulnerability Assessment Solution designed to serve Enterprises, Startups. Nessus provides end-to-end solutions designed for Windows. This online Vulnerability Management system offers Network Scanning, Vulnerability Assessment, Asset Discovery, Policy Management, Web Scanning at one place. Read Tenable Nessus Reviews
Explore various Tenable Nessus features, compare the pricing plans, and unlock the potential of seamless operations by selecting the right software for your business.
Features
View all Tenable Nessus Features- Policy Management
- Network Scanning
- Asset Discovery
- Prioritization
- Vulnerability Assessment
- Web Scanning
Tenable Nessus Caters to
- StartUps
- SMBs
- Agencies
- Enterprises
Emergents | 2024
Tools by Tripwire
Tripwire for Servers is a fully featured and best vulnerability assessment tool designed to serve SMEs, Enterprises. Tripwire for Servers provides end-to-end solutions designed for Windows. This online IT Management system offers Event Logs, Security Event Log, Server Monitoring at one place. Learn more about Tripwire
Explore various Tripwire features, compare the pricing plans, and unlock the potential of seamless operations by selecting the right software for your business.
Features
View all Tripwire Features- Security Event Log
- Event Logs
- Server Monitoring
Tripwire Caters to
- StartUps
- SMBs
- Agencies
- Enterprises
Emergents | 2024
Tools by Beeye
Retina Network Security Scanner is a fully featured Security Vulnerability Assessment Tool designed to serve Enterprises, Startups. Retina Network Security Scanner provides end-to-end solutions designed for Windows. This online Computer Security system offers Anti Spam, Real Time Monitoring, Security Event Log, Compliance Management, Vulnerability Protection at one place. Learn more about Retina Network Security Scanner
Explore various Retina Network Security Scanner features, compare the pricing plans, and unlock the potential of seamless operations by selecting the right software for your business.
- Anti Virus
- Anti Spam
Retina Network Security Scanner Caters to
- StartUps
- SMBs
- Agencies
- Enterprises
Emergents | 2024
Tools by F-Secure Corporation
F-Secure is a complete vulnerability assessment software that helps with virus protection, browsing protection, and parental control for children. It can support any size of businesses. It comes with a 30-days trial session having and is very fast, easy and simple to use. Learn more about F-Secure
Explore various F-Secure features, compare the pricing plans, and unlock the potential of seamless operations by selecting the right software for your business.
F-Secure Caters to
- StartUps
- SMBs
- Agencies
- Enterprises
Emergents | 2024
Tools by Qualys
Qualys Cloud Platform is a fully featured Vulnerability Assessment Tool designed to serve Enterprises, SMEs. Qualys Cloud Platform provides end-to-end solutions designed for Web App. This online Security Management system offers Vulnerability Scanning, Database Security Audit, Vulnerability Protection, Security Event Log, Compliance Management at one place. Learn more about Qualys Cloud Platform
Explore various Qualys Cloud Platform features, compare the pricing plans, and unlock the potential of seamless operations by selecting the right software for your business.
- Security Event Log
- Audit Trail
- Database Security Audit
- Compliance Management
- Vulnerability Protection
- Financial Data Protection
- Vulnerability Scanning
Qualys Cloud Platform Caters to
- StartUps
- SMBs
- Agencies
- Enterprises
Emergents | 2024
Tools by Rapid7
InsightVM is a fully featured Vulnerability Assessment Tool designed to serve Startups, Agencies. InsightVM provides end-to-end solutions designed for Web App. This online Vulnerability Management system offers Risk Management, Policy Management, Asset Discovery, Network Scanning, Vulnerability Assessment at one place. Learn more about InsightVM
Explore various InsightVM features, compare the pricing plans, and unlock the potential of seamless operations by selecting the right software for your business.
Features
View all InsightVM Features- Policy Management
- Network Scanning
- Vulnerability Assessment
- Asset Tagging
- Patch Management
- Risk Management
- Prioritization
- Asset Discovery
InsightVM Caters to
- StartUps
- SMBs
- Agencies
- Enterprises
Emergents | 2024
Tools by GFI Software
GFI Languard is a patch management system used by businesses for scanning and identifying network vulnerabilities in advance. This vulnerability testing tool also offers useful features such as inventory assessment, compliance management, TCO management, and change management. Learn more about GFI LanGuard
Explore various GFI LanGuard features, compare the pricing plans, and unlock the potential of seamless operations by selecting the right software for your business.
Features
View all GFI LanGuard Features- Vulnerability Scanning
- Server Monitoring
- Network Wide Management
- Network Diagnosis
- Scheduled Deployment
- Network Resource Management
- Automatic Scans
- Bandwidth Monitoring
GFI LanGuard Caters to
- StartUps
- SMBs
- Agencies
- Enterprises
Emergents | 2024
Tools by Beyond Security
beSECURE (AVDS) is a fully featured Vulnerability Assessment Tool designed to serve Agencies, SMEs. beSECURE (AVDS) provides end-to-end solutions designed for Windows. This online Security Management system offers Vulnerability Scanning at one place. Learn more about beSECURE (AVDS)
Explore various beSECURE (AVDS) features, compare the pricing plans, and unlock the potential of seamless operations by selecting the right software for your business.
Features
View all beSECURE (AVDS) Features- Internet Security
- Vulnerability Scanning
- User Management
- Password Protection
- Vulnerability Protection
- Basic Firewall
beSECURE (AVDS) Caters to
- StartUps
- SMBs
- Agencies
- Enterprises
Emergents | 2024
Tools by BeyondTrust Corporation
Beyond trust, help desk software provides privileged access and defend against threat related to unwanted remote access. Its flexible design simplifies the integration, maximize security and enhance user productivity. Learn more about BeyondTrust
Explore various BeyondTrust features, compare the pricing plans, and unlock the potential of seamless operations by selecting the right software for your business.
Features
View all BeyondTrust Features- Session Recording
- IT Asset Management
- Alerts/Escalation
- Dashboard
- Issue Tracking
- Knowledge Base Management
- Real Time Chat
- Ticket Management
BeyondTrust Caters to
- StartUps
- SMBs
- Agencies
- Enterprises
Emergents | 2024
Tools by VigiTrust
VigiTrust is a fully featured Vulnerability Assessment Software designed to serve Enterprises, SMEs and StartUps. VigiTrust provides end-to-end solutions designed for Web App and Android. This online Accreditation Management system offers Collaboration and Compliance management at one place. Learn more about VigiTrust
Explore various VigiTrust features, compare the pricing plans, and unlock the potential of seamless operations by selecting the right software for your business.
Features
View all VigiTrust Features- Reviewer Portal
- Workflow Management
- Collaboration
- Higher Education
- Document Management
- Compliance management
- Requirements Management
VigiTrust Caters to
- StartUps
- SMBs
- Agencies
- Enterprises
Emergents | 2024
Next Generation Vulnerability Management is the ne
In 2020, our company secured a place in the Forbes Top 100 Great People Manager by GMI. At present, Trishneet runs a successful cybersecurity endeavor with some of the biggest companies as their clients. Learn more about ESOF VMDR
Explore various ESOF VMDR features, compare the pricing plans, and unlock the potential of seamless operations by selecting the right software for your business.
Features
View all ESOF VMDR Features- Maintenance Scheduling
- Real Time Monitoring
- Asset Tagging
- Patch Management
- Prioritization
- Risk Management
- Web Scanning
- Whitelisting / Blacklisting
Pricing
Essential
$ 500
Single Device
ESOF VMDR Caters to
- StartUps
- SMBs
- Agencies
- Enterprises

It is very significant to safeguard your firm's networks, systems, and applications to prevent cyber threats. Utilizing vulnerability assessment tools like Microsoft baseline security analyzer can help in detecting and resolving weaknesses before they are taken advantage of by malicious actors.
This comprehensive guide will explore the leading vulnerability scanners currently offered, detailing their features, pros, and cons to assist you in selecting the most suitable tool for your organization's security requirements.
What are Vulnerability Assessment Tools?
Vulnerability assessment tools are computer software that is created to recognize, categorize, and give priority to susceptibilities in computer systems, network infrastructure, and applications. These vulnerability assessment scanning tools automatically search for new and existing hazards that can aim at an application.
Vulnerability management tools actively look for weaknesses in the network or system, identify them, and offer remediation tips to prevent the onset of a security breach.
They also involve vulnerability scanners for web applications, protocol scanners, and web application scanners. The aim of these vulnerability scanners is to assist establishments in detecting security flaws that may leave them susceptible to cyber threats or hazards. Numerous vulnerability scanners are obtainable, and several of the top-quality ones are listed on diverse websites.
Advantages of the Best Vulnerability Assessment Tools
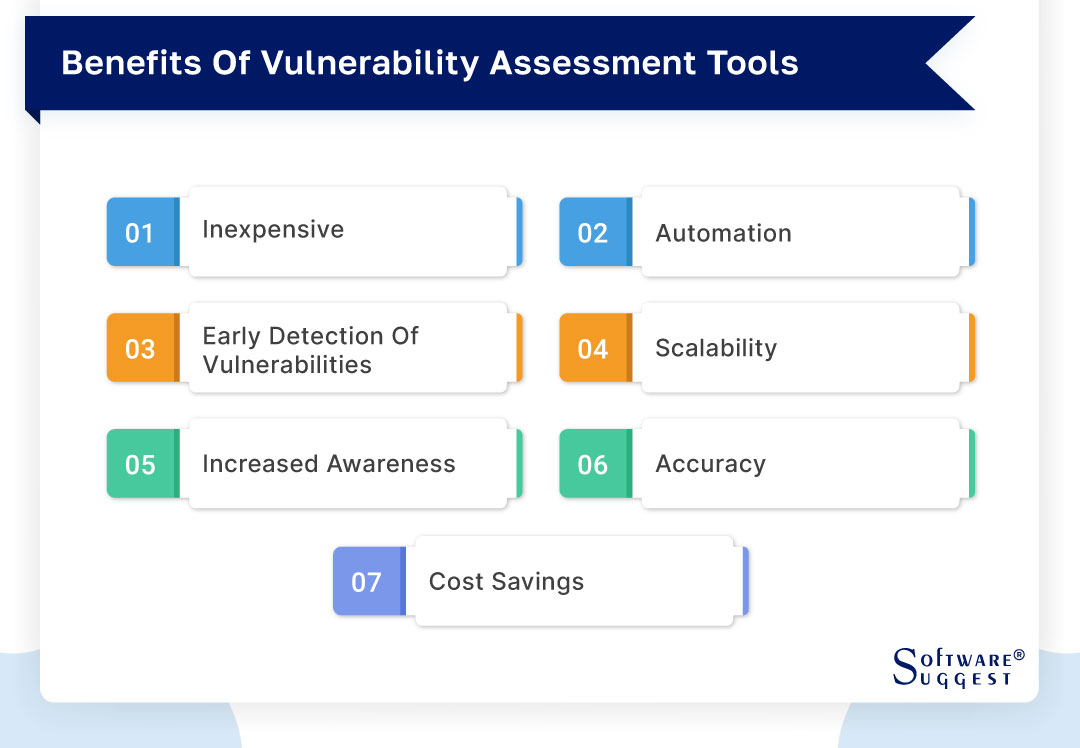
Vulnerability assessment scanning tools are gaining more popularity among businesses that aim to secure their networks and systems. This automated vulnerability assessment software is made to check networks and detect possible weaknesses that may be taken advantage of by cyber attackers. They are a useful means to enhance a firm's network security and safeguard delicate information. Here we will see 7 benefits of vulnerability scanners.
-
Inexpensive
The main benefit of utilizing automated vulnerability assessment software is its affordability. A lot of these tools can be obtained for no cost or at a nominal fee. This feature makes vulnerability assessment software a fantastic option for establishments that have financial constraints. They allow for a cost-efficient approach to recognizing weaknesses and implementing corrective measures before cybercriminals take attack them.
-
Automation
An additional perk of using automated vulnerability assessment software is its ability to be automated, allowing it to scan networks and spot weaknesses without the requirement of human interference. This feature may greatly reduce the time and resources required by establishments. Rather than manually examining each device, vulnerability scanning tools can perform the task automatically. It also enables IT personnel to concentrate on other important responsibilities.
-
Early detection of vulnerabilities
Tools for assessing vulnerability scanning can support establishments in detecting vulnerabilities at an early stage. This is crucial because the sooner a vulnerability is detected, the simpler it is to rectify. By detecting vulnerabilities early, organizations can take remedial measures before hackers exploit them. This can assist in avoiding data breaches and other security incidents that can harm an organization's reputation.
-
Scalability
The adaptability of vulnerability assessment solutions makes them perfect for establishments of any size. They have the capability to examine networks of varying scales, ranging from small enterprises to large corporations. Moreover, these tools can execute scans on multiple devices simultaneously, which is advantageous for organizations that have a multitude of devices within their network. The versatility of these tools allows them to be utilized by any organization, irrespective of its size.
-
Increased awareness
Tools for assessing vulnerability can also enhance your team's awareness of security concerns within an establishment. These vulnerability assessment solutions are capable of educating IT personnel and other workers on the significance of security by detecting vulnerabilities. This can foster a security-oriented atmosphere within an establishment, where all individuals are conscious of the perils and take measures to safeguard delicate information. This feature of creating awareness and maintaining security intact makes this solution a must-have for your team and overall business.
-
Accuracy
Vulnerability testing tools are equally precise. They employ advanced algorithms to scrutinize networks and recognize vulnerabilities. Consequently, the chances of overlooking vulnerabilities are lower than those in manual scanning methods. The precision of these vulnerability assessment tools can aid institutions in identifying vulnerabilities that could have been disregarded using manual techniques.
Information holds great significance and empowers modern businesses. Vulnerability tools render information more precise and amplify your business's overall efficiency.
-
Cost Savings
Ultimately, vulnerability testing solutions have the potential to support establishments in cost savings over time. By detecting vulnerabilities at an early stage and implementing necessary measures, organizations can avert expensive security breaches and other incidents.
Such actions can lead to savings worth millions of dollars in damages and lost revenue. Moreover, vulnerability management tools can assist establishments in complying with regulatory standards, thereby avoiding costly penalties and legal repercussions.
What is the Purpose Of Using Vulnerability Assessment Tools?
Tools for assessing vulnerability are crucial for companies seeking to boost their security stance and safeguard themselves against cyber risks. Such tools are created to scrutinize and evaluate computer networks, applications, and systems for security susceptibilities.
The key objective of utilizing vulnerability scanners is to recognize potential security hazards and shortcomings and rank them in order of importance for remedial action. Here we will delve deeper into the various objectives of leveraging vulnerability scanning tools.
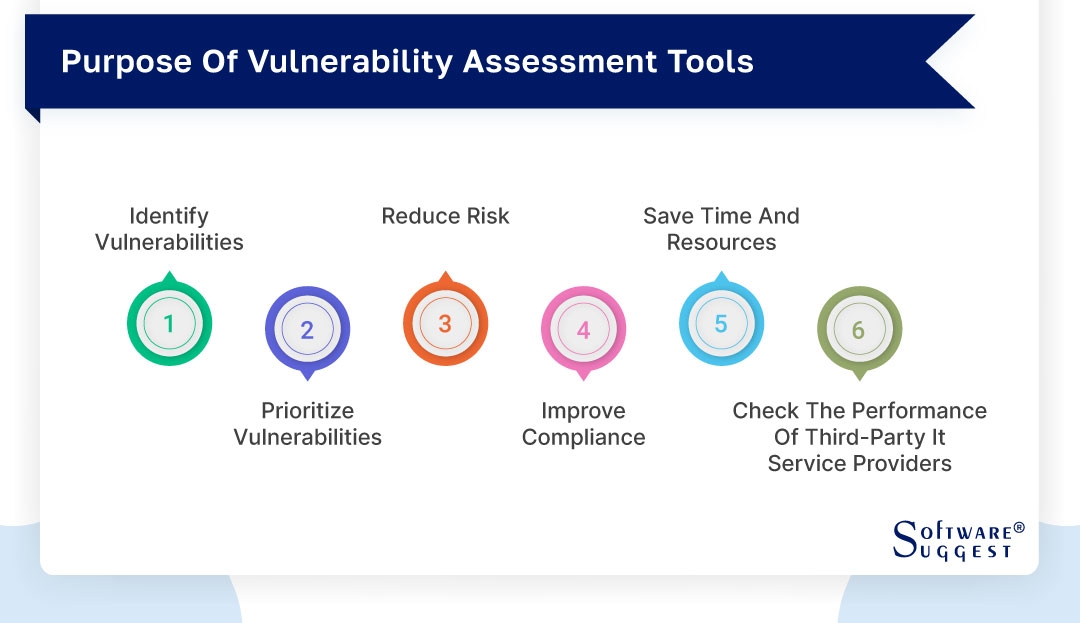
The following are some of the key purposes of using vulnerability scanners:
-
Identify vulnerabilities
The main aim of vulnerability testing tools is to identify flaws in the structures and connections of an establishment. These testing solutions utilize various methods to examine networks and structures. It also includes port exploration, susceptibility analysis, and infiltration testing.
By identifying weaknesses, establishments can implement corrective actions to reduce the likelihood of a security violation. This could contain installing patches, updating software, or adding additional security measures.
-
Prioritize vulnerabilities
After pinpointing weaknesses, vulnerability evaluation software can assist establishments in ranking their corrective measures depending on the seriousness of each vulnerability. These vulnerability testing tools offer institutions a risk rating for every vulnerability by taking into account aspects like the probability of exploitation and the probable effects of a successful attack. Such ranking enables institutions to concentrate on the most crucial vulnerabilities and swiftly implement corrective measures.
-
Reduce risk
Through the identification and ranking of susceptibilities, tools for assessing vulnerabilities assist institutions in decreasing their overall exposure to security breaches. These vulnerability assessment scanning tools offer establishments a thorough evaluation of their security status, enabling them to pinpoint shortcomings and implement corrective measures before a perpetrator can take advantage of them. In this way, they can safeguard confidential information, avert financial damages, and uphold customer confidence.
-
Improve compliance
Several regulatory frameworks mandate that organizations perform frequent vulnerability appraisals. By utilizing vulnerability assessment software, organizations can confirm adherence to compliance requirements and evade expensive penalties and legal repercussions.
Vulnerability assessment software can furnish organizations with comprehensive reports on their security status, comprising details on vulnerabilities, corrective actions, and risk evaluations. This data can be employed to prove compliance with regulatory requirements and industry benchmarks.
-
Save time and resources
Vulnerability testing software automates the process of scanning and saves firms a considerable amount of time and resources. Automated scans help to rapidly and accurately identify vulnerabilities, allowing IT personnel to concentrate on other essential duties. These tools can also offer organizations a unified perspective of their security status, eliminating the need to gather and scrutinize data from various sources manually.
-
Check the performance of third-party IT service providers
Establishments frequently depend on external IT service suppliers to handle their networks and systems. Nevertheless, these suppliers may implement distinct policies and methodologies for security that jeopardize the data and systems of the establishment.
Through the utilization of network vulnerability tests, establishments can assess the efficiency of their external suppliers and detect any probable weaknesses in their networks and systems. This aids establishments in guaranteeing that their associates are upholding adequate security measures to safeguard their data and systems and prevent any possible security incidents or breaches.
Steps to Implement Vulnerability Assessment Tools
The evaluation of vulnerability testing tools holds immense significance in maintaining the safety and sustainability of an organization's IT framework. This procedure encompasses the identification of susceptibilities and shortcomings present in the IT infrastructure and the adoption of suitable measures to counteract them.
Vulnerability assessment scanning tools play a pivotal role in this process, and its implementation demands meticulous planning and execution. This write-up elucidates the essential stages that one must follow while employing a tenable network security assessment tool.
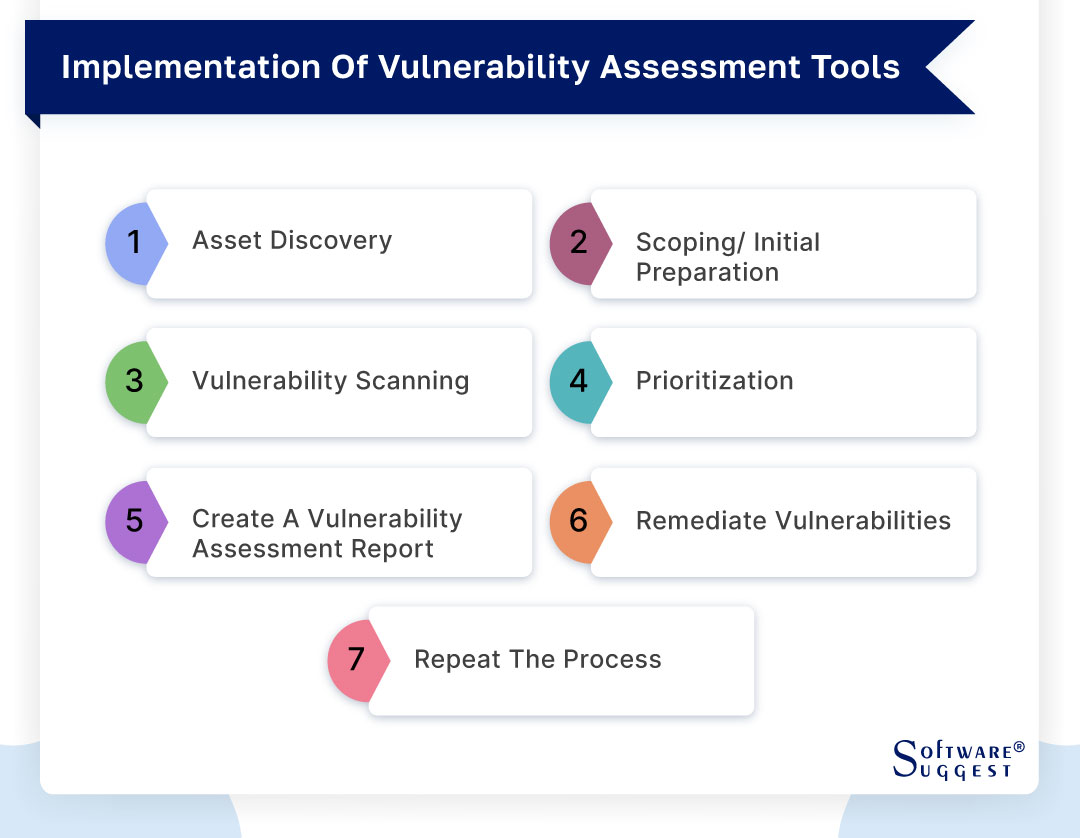
Step 1- Asset discovery
To initiate the use of the security vulnerabilities assessment tool, the foremost step is to recognize all the elements in the IT infrastructure that require assessment. These comprise physical devices like servers, routers, and switches, along with software applications and databases. The exploration of assets can be accomplished through multiple means, including network scanners, inventory tools, and detection agents.
Step 2- Scoping/ initial preparation
The following stage is to determine the scope of the vulnerability assessment after the assets have been identified. This comprises determining the assets that need evaluation, the requisite level of assessment, and the completion date. The importance of the assets, their level of sensitivity, and the possible consequences for the establishment if they are compromised should all be taken into account when determining the assessment's scope.
Additionally, setting up the testing requires acquiring the necessary resources, permits, and authorizations. This entails getting approval from senior management, procuring funding, and obtaining the necessary login information and access rights for the evaluation instrument.
Step 3- Vulnerability scanning
The next phase is to execute a vulnerability assessment on the recognized resources. Vulnerability assessment includes deploying automated software to examine the resources for susceptibilities and flaws. The assessment operation can be accomplished by utilizing diverse tools, such as network scanners, web application scanners, and database scanners.
Throughout the assessment operation, the vulnerability assessment tool will recognize susceptibilities and flaws that can be manipulated by assailants. The software will also furnish details on the severity of the susceptibilities, the possible impact on the resource, and the suggested remedial actions.
Step 4- Prioritization
After identifying the vulnerabilities, the subsequent stage is to arrange them in order of importance, taking into account their severity and potential impact on the organization. This includes classifying the vulnerabilities according to their significance, the probability of being exploited, and the potential consequences for the organization if exploited.
The prioritization procedure enables concentration on the most significant vulnerabilities initially and guarantees that restricted resources are assigned to the most critical concerns. Moreover, the prioritization process considers the potential effect of remedial actions on the organization's operations and systems.
Step 5- Create a vulnerability assessment report
The subsequent phase entails generating a report on vulnerability assessment. The report presents a summary of the assessment procedure, the detected susceptibilities, and the suggested corrective measures. It is imperative that the report is lucid, succinct, and comprehensible and that it comprises comprehensive particulars on the vulnerabilities, their gravity, and their probable repercussions.
In addition, the report must propose remedial activities that must be executed to alleviate the detected vulnerabilities. It should also encompass a schedule for the remedial actions, along with the roles and obligations of the concerned parties involved in the remedial process.
Step 6- Remediate vulnerabilities
The next phase is to resolve the pinpointed susceptibilities. Resolving the susceptibilities encompasses undertaking suitable measures to alleviate the identified susceptibilities and shortcomings. This may encompass installing patches, upgrading software, and modifying configuration settings.
The resolution procedure should be meticulously strategized and implemented to downsize any influence on the enterprise's operations and systems. It is equally crucial to evaluate the resolution activities to ensure that they are efficient and do not induce fresh susceptibilities or shortcomings.
Step 7- Repeat the process
The last step is to carry out periodic vulnerability assessments. This guarantees that the IT infrastructure of the organization stays safe and dependable as time goes by. Regular vulnerability assessments also enable the discovery of fresh weaknesses and vulnerabilities that may have been introduced by new software, devices, or modifications to the IT infrastructure.
Based on the organization's risk profile, the rate of change in the IT infrastructure, and the possible effects of new vulnerabilities on the organization, the frequency of vulnerability assessments should be decided. Vulnerability assessments should generally be carried out at least once a year, while in high-risk contexts, more regular assessments may be required.
Different Types Of Vulnerability Assessment Tools
Here are different classifications of vulnerability assessment tools depending on the systems they target. This write-up will enumerate various kinds of vulnerability assessment tools, such as wireless, cloud, network, IoT, database, host, and application scanning tools.
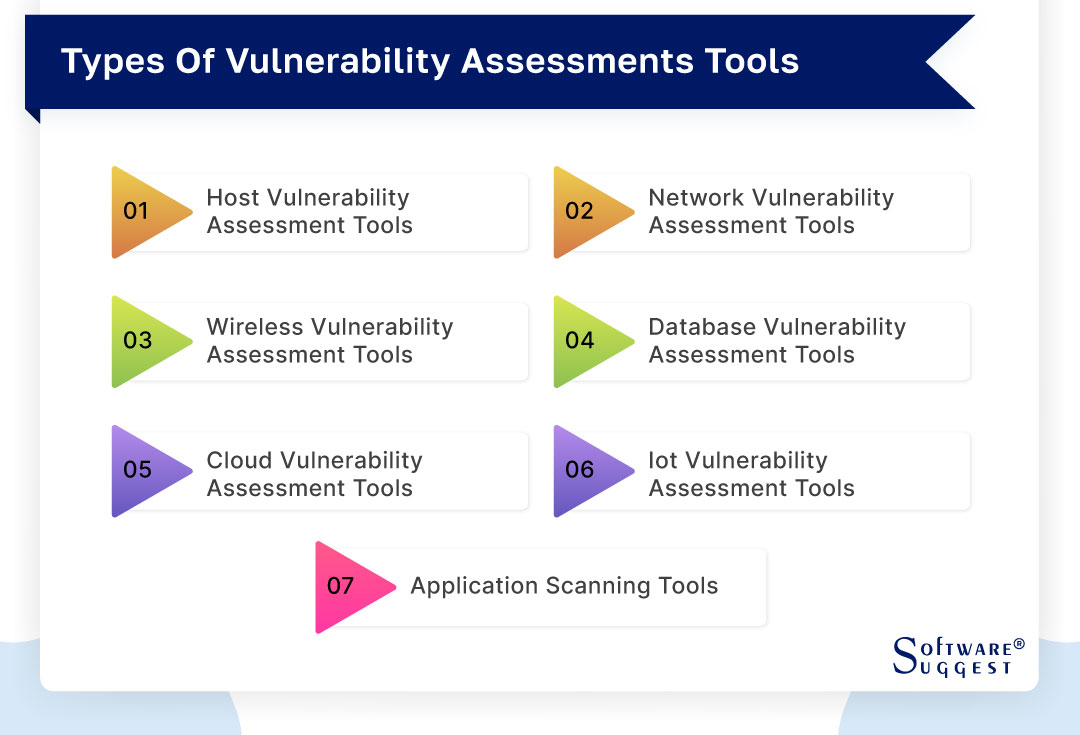
-
Host vulnerability assessment tools
Host vulnerability assessment tools aim to scrutinize and detect vulnerabilities in single servers or computers. They usually evaluate the operating system, system configuration, and installed software to identify possible vulnerabilities. Qualys, Nessus, and OpenVAS are some of the host vulnerability assessment tools available.
-
Network vulnerability assessment tools
The infrastructure of a network is examined and evaluated using vulnerability assessment solutions for network vulnerability. It consists of things like switches, routers, firewalls, and other network hardware. These security vulnerability assessment testing tools carefully examine network traffic and system configuration to find any potential security flaws. Retina, Nexpose, and Nmap are a few popular tools for evaluating network vulnerabilities.
-
Wireless vulnerability assessment tools
Tools for assessing wireless vulnerabilities are created to scan and find weaknesses in wireless networks, particularly Wi-Fi networks. To find potential security flaws, these solutions often assess the wireless network protocols, encryption techniques, and access points. Solutions for assessing wireless vulnerabilities include Wireshark, Kismet, and Aircrack-ng.
-
Database vulnerability assessment tools
Tools for evaluating database vulnerability are utilized to examine and detect susceptibilities in database management systems (DBMS) like Oracle, MySQL, and Microsoft SQL Server. These vulnerability assessment tools usually scrutinize the database setup, authorization controls, and saved procedures to recognize possible security problems. AppDetective, DbProtect, and Imperva are a few instances of database vulnerability assessment tools.
-
Cloud vulnerability assessment tools
The purpose of cloud vulnerability evaluation software is to inspect and detect susceptibilities in cloud-oriented systems like Amazon Web Services (AWS), Microsoft Azure, and Google Cloud Platform. Security vulnerability assessment tools generally scrutinize the cloud framework, virtual machines, and network configurations to pinpoint probable security concerns. CloudSploit, Aqua Security, and Dome9 are some of the well-known cloud vulnerability evaluation tools.
-
IoT vulnerability assessment tools
Tools for evaluating the susceptibility of IoT devices, such as smart home appliances, wearables, and industrial control systems, are employed to scan for and pinpoint vulnerabilities. These tools usually inspect the firmware of the devices, network protocols, and data transmission to detect potential security concerns. Nessus, Shodan, and IoT Inspector are a few instances of IoT vulnerability assessment tools.
-
Application scanning tools
Tools for scanning applications are created to detect and recognize weaknesses in web applications and software programs. Generally, these tools scrutinize the application code, inputs, and outputs to detect any probable security concerns. Burp Suite, AppSpider, and IBM AppScan are some commonly used application scanning tools.
Factors to Choosing a Vulnerability Assessment Tool
In the contemporary era, where enterprises and establishments are perpetually exposed to cyber hazards, vulnerability evaluation utilities have become a crucial component of their security apparatus. These utilities furnish significant perspectives into an establishment's security stance and facilitate the detection of vulnerabilities that necessitate attention.
Nevertheless, the market offers numerous alternatives, making it arduous to select the appropriate vulnerability assessment utility. Here, we will deliberate on the aspects that one should contemplate while picking a vulnerability assessment tool.
-
User-friendliness
The main factor to think about when choosing a vulnerability testing tool is how user-friendly it is. Finding a tool that is easy to use and navigate is vital because it will save you time and effort. You will be able to concentrate on checking weaknesses rather than battling with the tool. Seek tools with a straightforward user interface and those that offer clear instructions and direction.
-
Features
The subsequent factor to consider is the tool's offered features. A good vulnerability assessment tool should provide extensive coverage of vulnerabilities and security risks. It should be capable of scanning all sorts of systems and networks, including web applications, databases, and mobile devices.
The vulnerability assessment tool should also be able to detect both known and unknown vulnerabilities and offer remediation guidance. Search for tools that provide advanced features such as threat intelligence, machine learning, and artificial intelligence.
-
Coverage
The scope of vulnerability assessment software is a crucial aspect to contemplate. The software must possess the capability to examine all sorts of networks and systems, encompassing those based on the cloud and those that are hybrid. It should also have the ability to examine various operating systems and platforms. Ensure that the software you select covers all the sections of your enterprise that necessitate vulnerability scanning.
-
Customer support
When selecting vulnerability assessment software, it is imperative to consider the quality of customer service. Seek out software that provides exceptional customer support, comprising phone, email, and live chat assistance. Additionally, the vulnerability assessment tools should have a comprehensive knowledge repository and user forums where you can obtain solutions to common queries and problems.
-
Compliance
Compliance is a crucial factor for numerous institutions, notably those that function in regulated sectors like healthcare and finance. Seek vulnerability evaluation instruments that conform to pertinent regulations and criteria, like HIPAA, PCI DSS, and ISO 27001. Conformance with these criteria certifies that the instrument satisfies the required security and confidentiality prerequisites.
-
Regular scans
Regular scans are vital to upholding your organization's security. Look for vulnerability assessment tools that offer routine, programmed scans. The instrument ought to enable you to arrange scans on a timetable and dispatch notifications when novel vulnerabilities are detected. Regular scans ensure that you are always aware of security hazards and can take swift action to rectify them.
-
Ease of use
Another crucial aspect to take into account when selecting a vulnerability testing tool is the ease of use. The tool must have simple installation and configuration instructions as well as clear user manuals. Also, it should be simple to combine with your current security tools and architecture. A simple-to-use tool will save you time and effort while allowing you to concentrate on patching vulnerabilities.
-
Detailed reporting
In-depth reporting is vital to comprehend the outcomes of vulnerability scans and take corrective action. Choose vulnerability assessment tools that offer extensive reports, such as details of the identified vulnerabilities, their severity levels, and remedial measures. The tool must also provide graphical representations, like charts and graphs, to help you interpret the data.
-
Integrations
For vulnerability testing tools to function efficiently, it is necessary to have integrations with your current security framework. Ensure that the testing tools you pick can easily integrate with your security tools, like intrusion detection systems, firewalls, and security information and event management (SIEM) solutions. Also, the tool must be able to integrate with other third-party tools like ticketing systems and asset management tools.
-
Cost & budget
Furthermore, when selecting a vulnerability assessment tool, cost and budget are crucial factors to consider. Search for tools that offer value for money and are within your budget. Evaluate the total cost of ownership, including maintenance, licensing, and support costs. Some testing tools provide a free trial or a limited free version, which can help you assess the tool's effectiveness before purchasing it.
Top 5 Vulnerability Assessment Tools Comparison
As the frequency of cyber hazards increases, it is imperative to have vulnerability testing solutions to safeguard establishments. These software programs can recognize weaknesses in networks, applications, and systems, allowing organizations to take immediate action to rectify them.
Given the plethora of options available, it can be tough to select the appropriate tool for your organization. In this article, we will explore the 5 best vulnerability assessment tools currently available.
1. OpenVAS
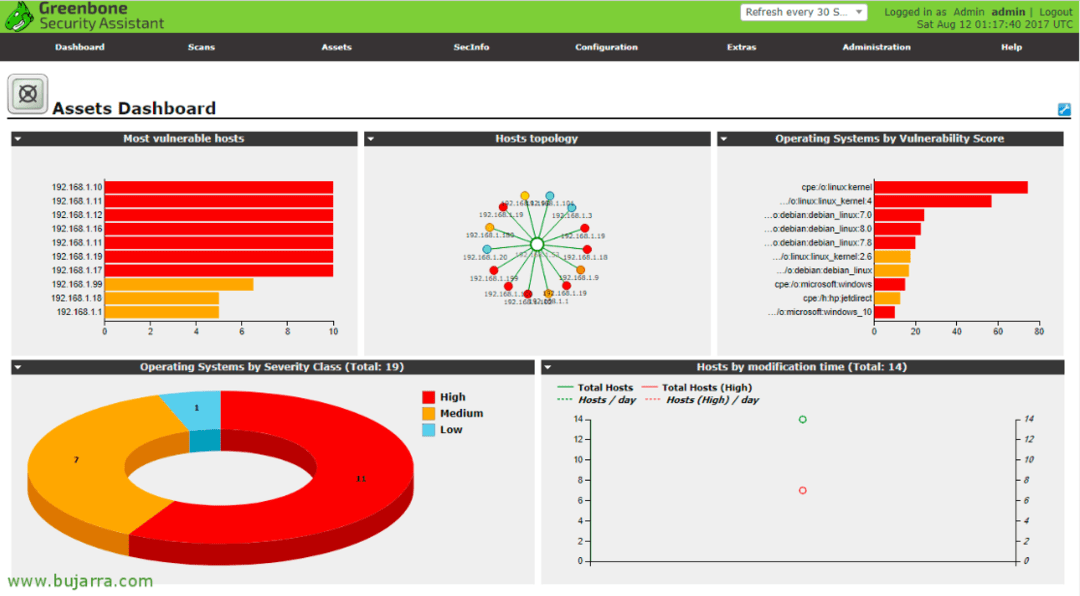
OpenVAS is a well-known open-source solution used for identifying network and system vulnerabilities. This testing tool comes with a user-friendly web-based interface that allows users to schedule scans, configure them, and view reports. With OpenVAS, detecting vulnerabilities across various operating systems and applications is possible, which makes it versatile software. Additionally, it features a robust scripting language that enables users to personalize scans and build custom plugins.
Features
- Monitor problems as weaknesses are detected
- Explore software and systems for certain regulatory demands
- Conduct practical simulations and breach tests
- Scan operational applications externally for security flaws
Pros
- Powerful automation capabilities
- User-friendly GUI
- Large-scale scans are done easily
Cons
- The input method can be a bit annoying for beginner users
- PDF report generation breaks sometimes
Pricing
- Click Here to know more about pricing.
2. Acunetix
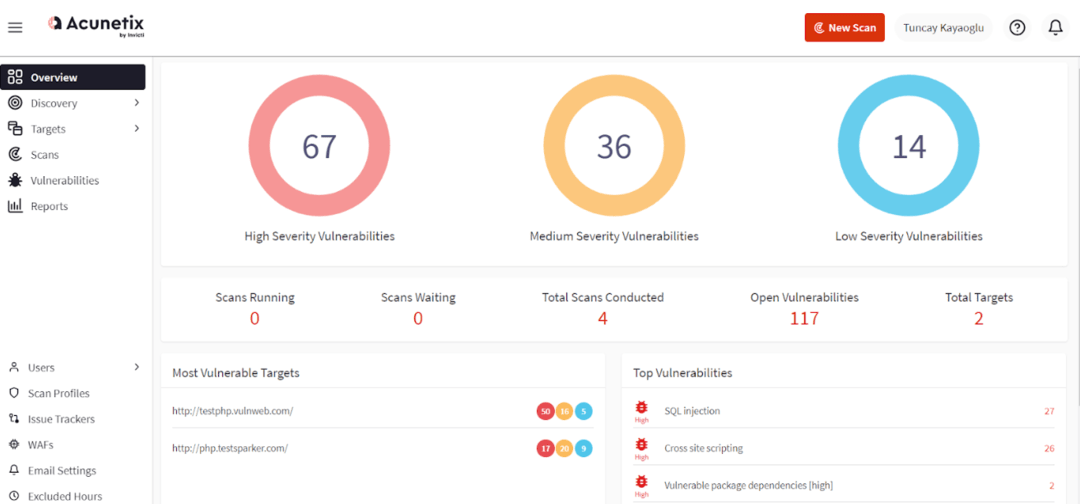
Invicti Security's Acunetix is a vulnerability assessment tool designed to enable global small and medium-sized businesses to manage their web security effectively. Their aim is to equip security teams with the means to minimize risks associated with various web applications through swift scans, detailed outcomes, and smart automation. They recognize that the right tools can foster a security-oriented culture by bridging the gap between security and development, reducing blame games, friction, and the need for rework.
Features
- Explores SPAs, sites with an abundance of scripts, and applications that are constructed with HTML5 and JavaScript
- Creates macros to mechanize the scanning process in areas that are password-protected and difficult to access
- Scans the unassociated files that are invisible to other scanning tools
Pros
- Helps avoid loss of time on incorrect security alerts by providing proof of the attack
- Identifies the specific code segments that require rectification
- Helps developers to address security concerns independently
- Identifies 7,000 + web vulnerabilities
Cons
- Single Page applications lack in-depth information
- Difficult to personalize the analyses
Pricing
- Click Here to know more about the pricing.
3. Intruder
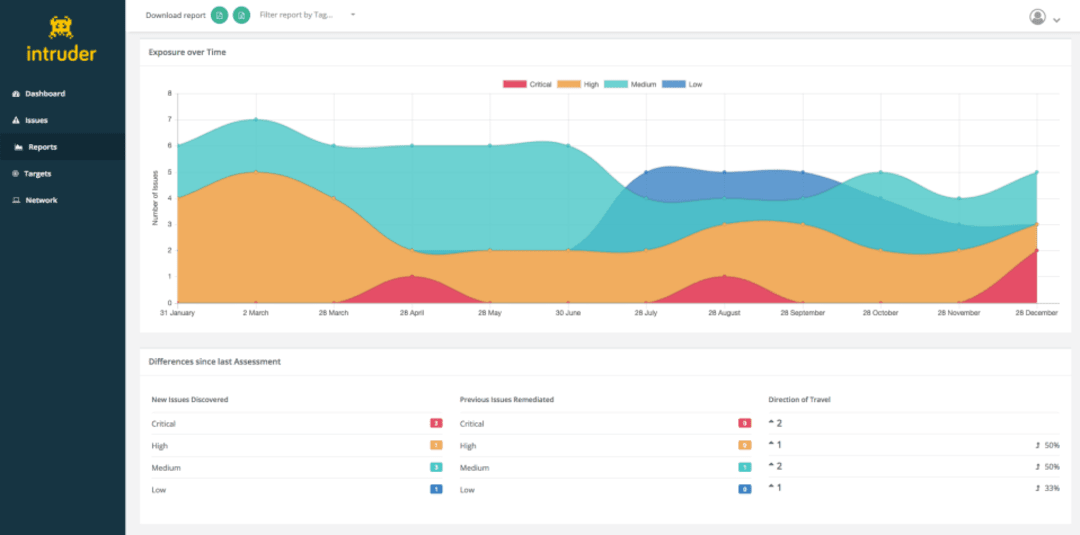
Founded in 2015, Intruder is a vulnerability assessment solution establishment that seeks to address the problem of excessive data in vulnerability management. This vulnerability scanner, which is based on the cloud, is customized to detect vulnerabilities in networks and web applications. The system provides a simple user interface that enables users to schedule scans effortlessly and obtain reports. Intruder employs artificial intelligence and machine learning to improve the accuracy of its scans and decrease the likelihood of erroneous findings.
Features
- Enhanced scope with top-notch proficiency
- Decreased duration from identifying vulnerability to resolution
- Certified penetration testers for vulnerability prioritization
- Safeguard your developing technology landscape
- Receive notifications on alterations in open ports and services
Pros
- Provides integrations with popular issue trackers
- Auto scanning with AI
- New vulnerability detection
- Alert levels
- Offers 14-day free trial
Cons
-
Report generation needs more details
Pricing
- Pricing starts at $101 per month for 1 target license.
4. Nikto
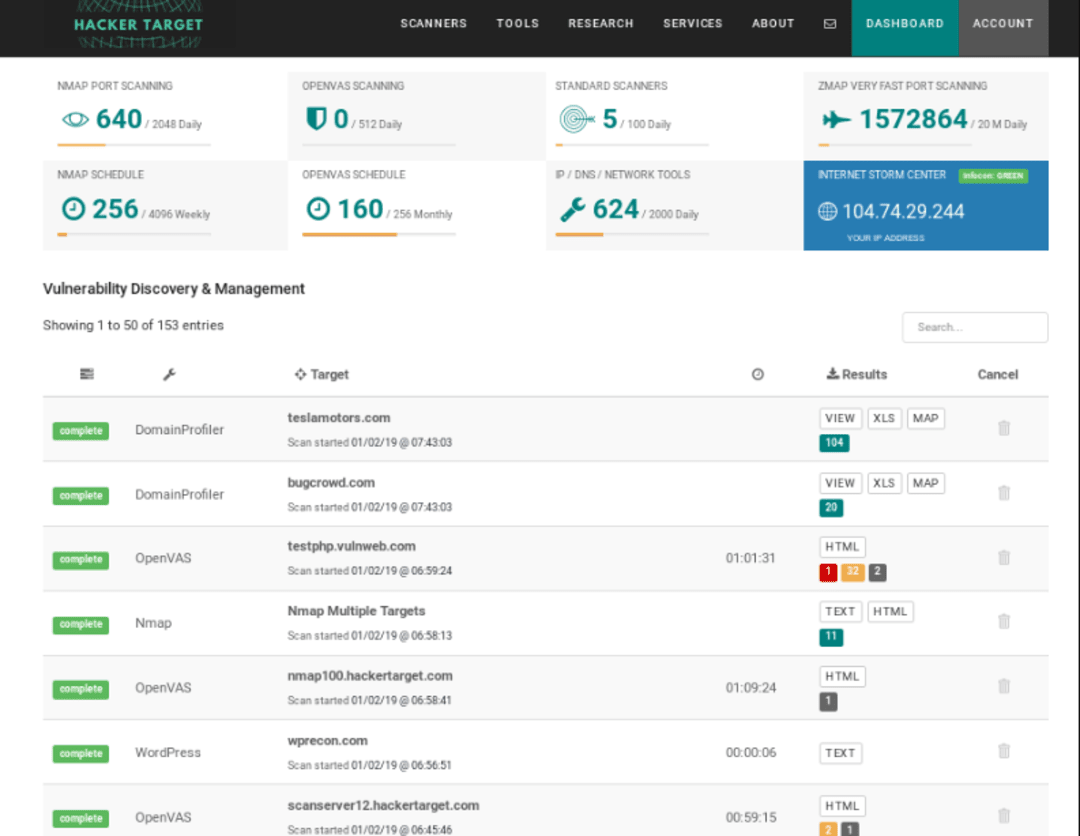
Nikto is a freely available vulnerability assessment tool for examining web servers, which is intended to recognize weaknesses in them. It has the capability to recognize a broad range of vulnerabilities, such as obsolete software versions, servers that are not configured properly, and CGI scripts that are vulnerable. Nikto is user-friendly and offers a command-line interface that enables users to customize scans and examine reports.
Features
- Recognizes software that is installed through headers, favicons, and files
- Authenticates hosts using Basic and NTLM
- Attempts to guess subdomains
- Identifies usernames in Apache and cgiwrap
- Uses mutation techniques to search for content on web servers
Pros
- Impressive speed and efficiency
- Free to use
- Provides detailed reports on detected vulnerabilities
Cons
- There must be a group of users
- Assistance must be accessible
Pricing
- Nikto is free to use.
5. Invicti
Invicti Security is a dominant supplier of web app security solutions that assist establishments in recognizing and resolving flaws in their web apps. Having more than ten years of expertise, Invicti presents an all-inclusive range of vulnerability evaluation instruments, which includes web, network, and mobile app scanners.
The objective of the organization is to assist clients in securing their apps and safeguarding their sensitive information from online hazards. Invicti is acknowledged by businesses of all magnitudes, from startups to Fortune 500 corporations, and has gained several awards and honors for its inventive resolutions.
Features
- Thorough scanning of web applications to identify vulnerabilities
- Automated validation of vulnerabilities to minimize incorrect alerts
- Incorporation with frequently used DevOps utilities for effortless security integration
- Modifiable reports and dashboards for a comprehensive understanding of vulnerabilities
- Sophisticated scanning methods, such as machine learning and AI
Pros
- Easy to use and simplifies the process of assessing vulnerabilities
- Reports and dashboards that can be customized
- Seamless integration with popular DevOps tools
- Exceptional customer support
Cons
- It may not be affordable for smaller organizations with limited budgets.
- Some users may find the tool's advanced scanning techniques to be daunting or complicated to set up
Pricing
- Click Here to know the pricing.
Conclusion
To sum up, it is imperative to invest in a trustworthy vulnerability assessment tool to ensure the protection of your data and systems. There are various choices, and it is very significant to assess and pick the tool that is most suitable for your establishment's requirements and financial resources. You can always refer to this blog when you plan to purchase a vulnerability testing tool for your firm.





















